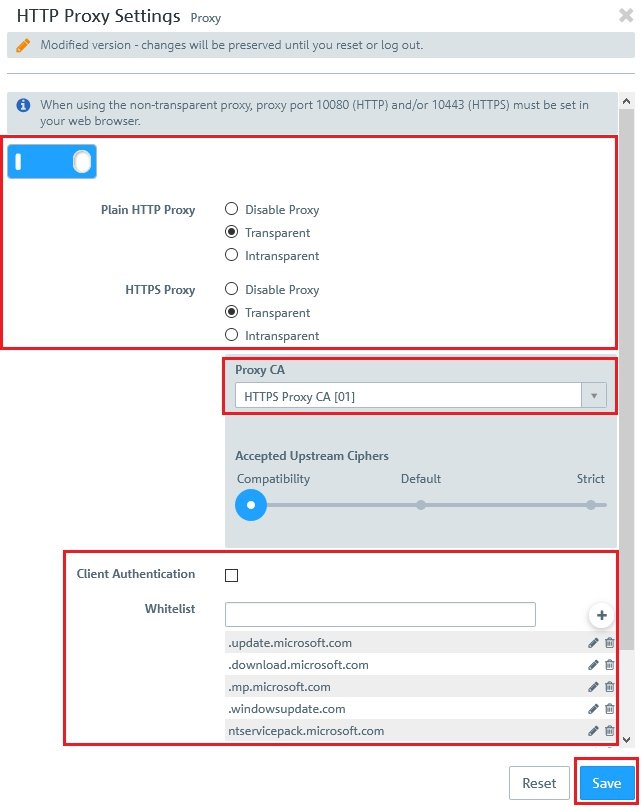
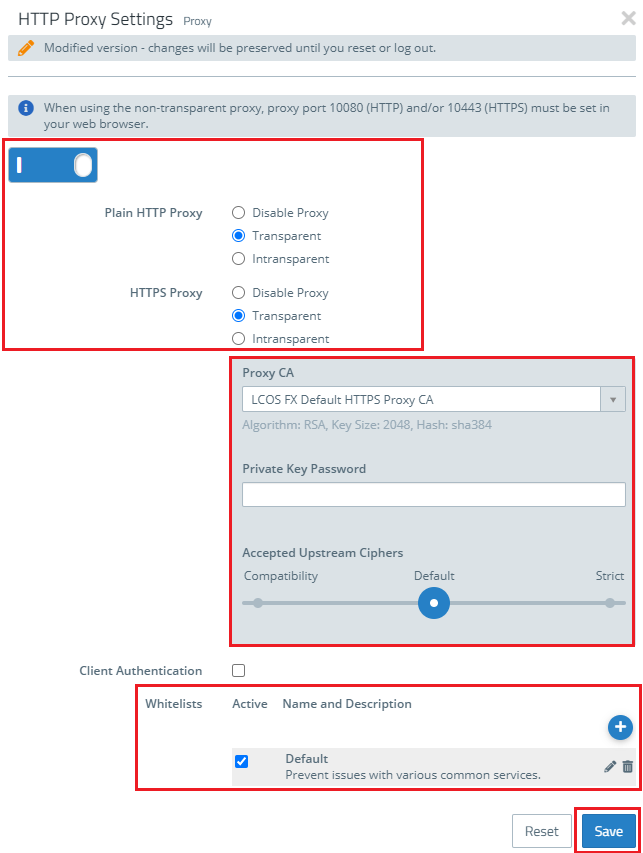
 Image Added Image Added2) Configure usage of the HTTP(S) proxy:In this example, the LAN contains Windows PCs that can access the Internet. Throughout the LAN, access to web pages is forced to go via the HTTP(S) proxy of the Unified Firewall. 2.1) In the host/network groups desktop object for the LAN, click the connection icon and then click the WAN network object. 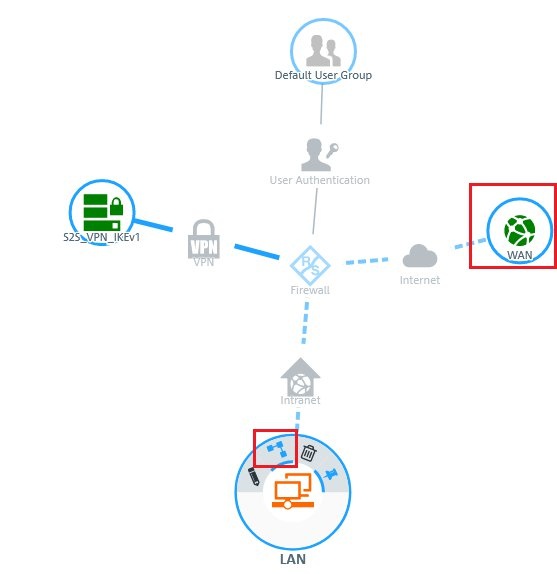 Image Modified Image Modified2.2) The dialog with the settings for this connection is opened. Now you have to click on the NAT option for the HTTP and/or HTTPS service. 2.3) Set a checkmark for the option Enable proxy for this service and click Save. 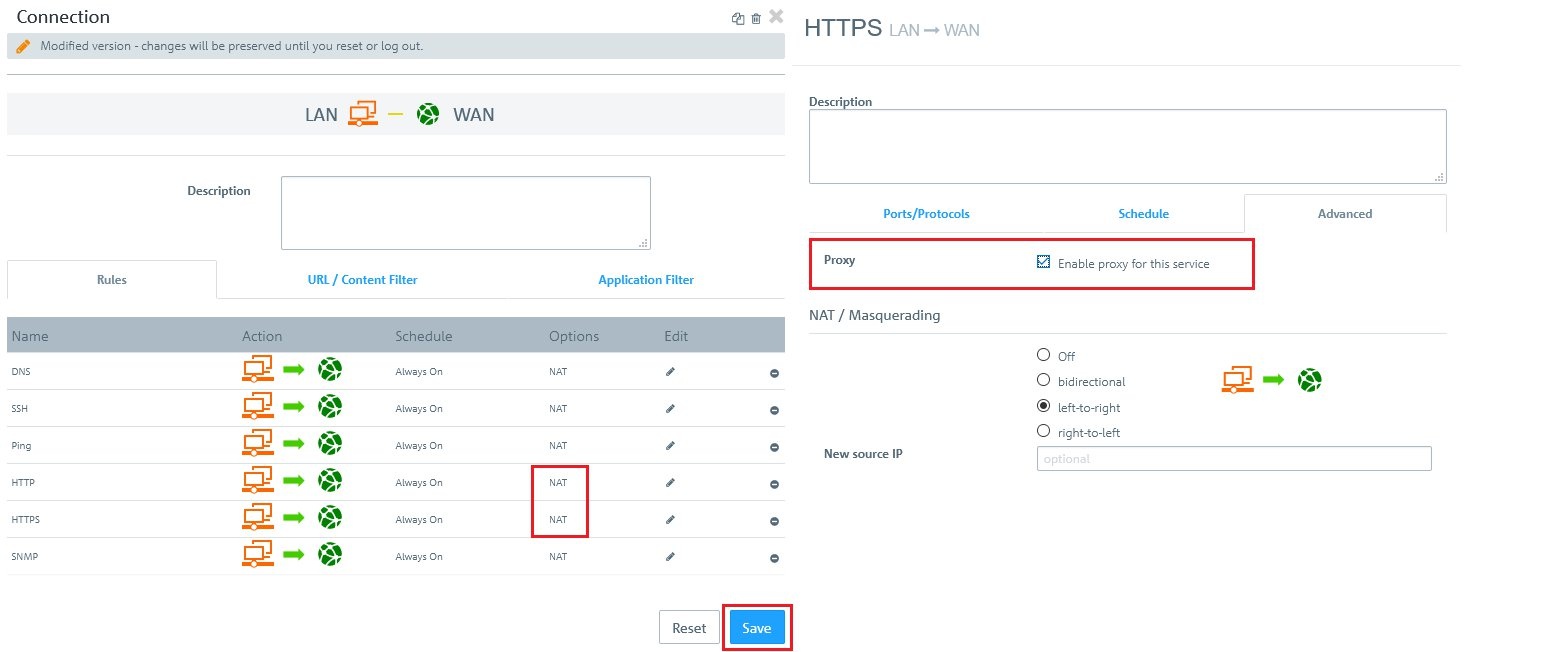 Image Modified Image Modified2.4) The entries in the list of services for HTTP and/or HTTPS should look like this.Click on Save again. 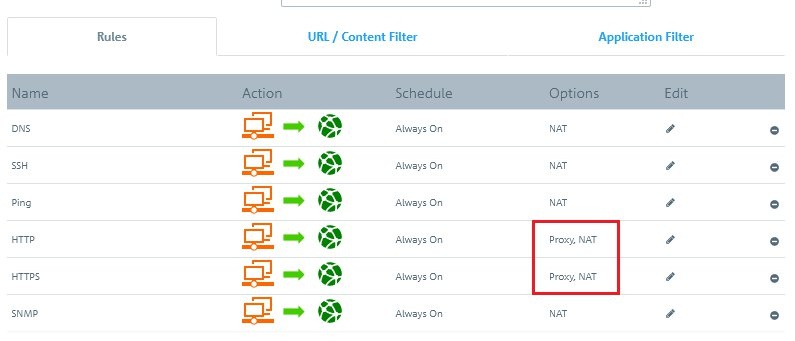 Image Modified Image Modified2.5) Finally, implement the configuration changes by clicking Activate in the firewall.  Image Modified Image Modified3) Export certificate and import it on a Windows PC:In this example, the LAN contains numerous Windows PCs that can access the Internet. Access should be directed via the HTTP(S) proxy of the Unified Firewall. 3.1) Go to the menu Certificate management → Certificates. 3.2)For the certificate of the LCOS FX Default HTTPS Proxy CA, click the export icon. 3.3) The certificate has to be exported in PEM/CRT format. Click the Export button to start the process. 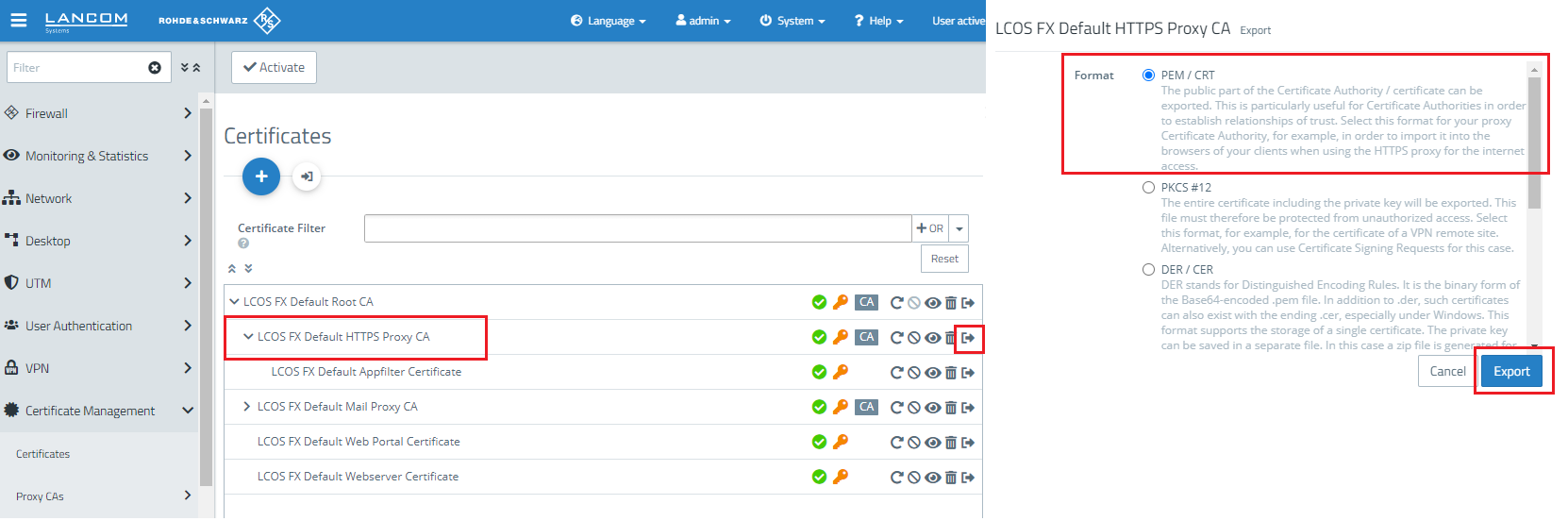 Image Modified Image Modified3.4) On your computer, go to the folder where you exported the certificate. 3.5) In order to install the certificate under Windows, change the file extension from *.pem to *.crt.
| Info |
|---|
| Please note that you must have administrator rights to install the certificate on a Windows system. |
3.6) Click the certificate file and acknowledge the subsequent security warning with OK. 3.7) In the Certificate dialog, select the option Install certificate. 3.8) In this example, the certificate installed on the local computer is to be used by all users of this computer. 3.9) Select the option Place all certificates in the following store, click Browse and select the Trusted root certification authorities store. 3.10) Click Next and continue until the Certificate Import Wizard is finished. 3.11) This concludes the certificate import. Any popular browser will be able to use the certificate after the computer is restarted. Repeat the certificate import procedure (steps 3.7 to 3.11) on all of the other computers in the LAN. | Info |
|---|
Note on using the certificate in Mozilla Firefox: Do the following to use the certificate in Mozilla Firefox: - Enter the following into the address bar of the browser: about:config.
- Search for the value security.enterprise_roots.enabled.
- Change the value from false to true.
- Restart the browser.
|
Information on the use of a pre-created and superordinate CA:If an end device trusts a pre-created and superordinate CA, it can be moved between sites without further effort This case is described in more detail below: 1) Creating the parent CA: This CA can be created on any LANCOM R&S®Unified Firewall. Ideally, this is done on a central firewall without Internet access. If a dedicated public-key infrastructure already exists, it is recommended to use it. | Info |
|---|
| We recommend that the parent CA is valid for at least 5 years. |
2) Rolling out the CA: This parent CA must be imported to all endpoints and renewed and replaced on all endpoints before expiration. 3) Creating and signing the proxy CAs on the individual LANCOM R&S®Unified Firewall: - A certificate signing request (CSR) for an intermediate CA is created locally on the individual LANCOM R&S®Unified Firewalls.
- The CSR must be signed centrally by the parent CA.
- The signed intermediate CA is imported into the local LANCOM R&S®Unified Firewall and selected as the CA for the HTTPS proxy.
|