...
| Info |
|---|
Access points that are operated in a WLC scenario must each be configured individually. A central configuration of the steps described here via a WLC is not possible. This scenario can also be implemented with LCOS LX access points. |
Requirements:
- LANCOM router as the RADIUS server
- Access point with LCOS
- Switch of the GS-3xxx series
- LCOS as of version 10.30 on the router which acts as RADIUS server (download latest version)
- LCOS as of version 9.24 on the access point (download latest version)
- LANtools as of version 10.30 (download latest version), 10.40 RU1 when configuring the access point via LANconfig
- Any web browser for accessing the web interface of the GS-3xxx and the access pointswitch
Scenario:
- A LANCOM router with the IP address 192.168.1.254 is operating as a RADIUS server.
- A switch of the GS-3xxx series with the IP address 192.168.1.250 is operating as a RADIUS authenticator. The switch therefore forwards the requests from the access point to the RADIUS server.
- An access point with LCOS presents its authorization credentials and logs on to the switch, thus acting as the RADIUS supplicant.
- After a successful login to the RADIUS server, the switch should enable communication on the port that the access point is connected to.
...
- IP address: Enter the switch IP address so that this it can authenticate itself as the RADIUS authenticator at the RADIUS server.
- Netmask: Enter the netmask 255.255.255.255. This stands for a single IP address.
- Protocols: Check that the protocol is set to RADIUS.
- Client secret: Enter a password that the switch uses to authenticate itself at the RADIUS server. This is entered on the switch in step 2.1.
...
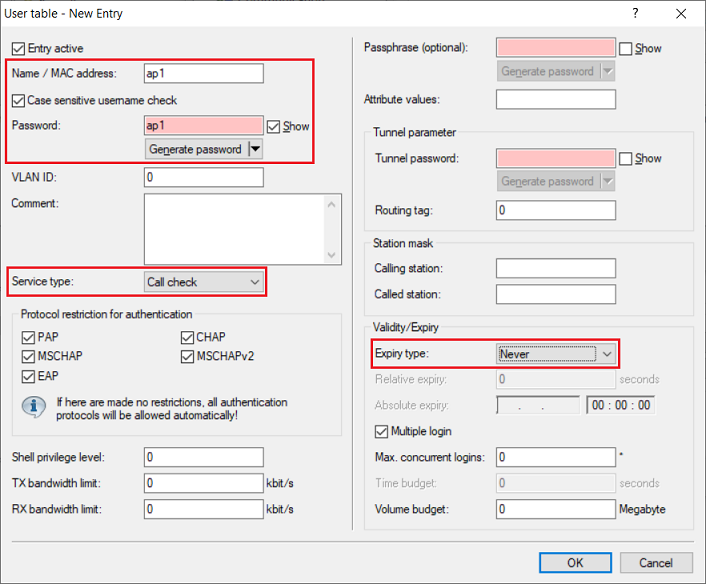
- Name / MAC address: Enter a user name that the access point uses to authenticate itself at the RADIUS server.
- Password: Enter a password that the access point uses to authenticate itself at the RADIUS server.
- Service type: From the drop-down menu, select Call -Checkcheck.
- Expiry type: From the drop-down menu, select Never so that the user account remains permanently valid.
| Info |
|---|
As of SWOS 4.00 RU2 the switch sends RADIUS requests with the Service type Call check. In this case the Service type in this menu als has to be set to Call check. As an alternative the option Any can also be selected. As of LCOS SX 4.00 RU5 the Service type Framed is used for RADIUS requests and the The Service type Call-Check is used for MAC-based requests. In this case the Service type has to be set to Framed. As an alternative the option Any can also be selected. The Service type Call check is supported as of LCOS 10.30. |
1.8) This concludes the configuration of the RADIUS server on the LANCOM router. You can now write the configuration back to the device.
...
- Hostname: Enter the IP address of the router that was set up as the RADIUS server in step 1.
- Key: Enter the Client secret set in step 1.5. The switch uses this password to authenticate itself at the RADIUS server.
...
| Info |
|---|
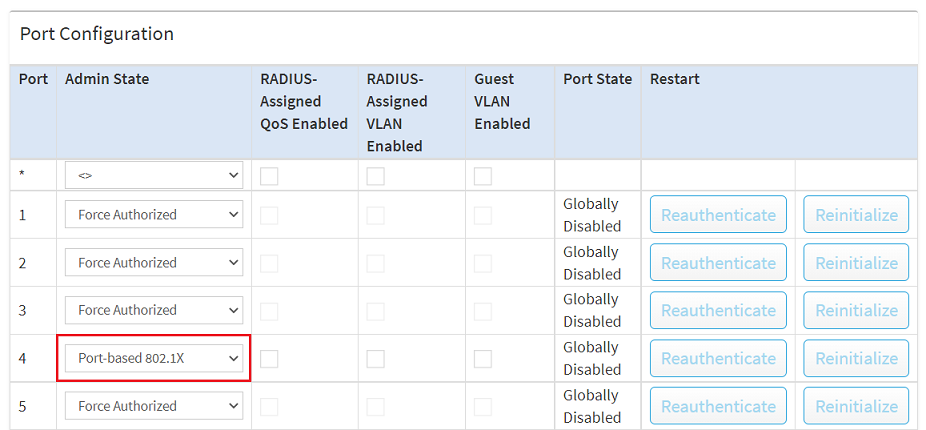
With the option Port-based 802.1X, solely the access point should be able to authenticate itself. All other end devices connected via WLAN can communicate via the switch port without authentication. For this reason it is important to provide the WLAN end devices with their own network that is separated from the management network by VLAN. You can use this Knowledge Base article to help you here. |
2.5) Click the red disk symbol on the upper right side to save the configuration as Start configuration.
...
3) Configuring the RADIUS supplicant on the access point:
In order for the access point to be able to authenticate at the RADIUS server of the WLAN controller, the authentication method must be set and user data have to be set for logging in. This example uses the authentication method PEAP/MSCHAPv2. The user data of the access point was configured on the router in step 1.7.
3.1) Connect to the access Point via CLI and switch to the path Supplicant-Ifc-Setup:
cd /Setup/LAN/IEEE802.1x/Supplicant-Ifc-Setup
3.2) Go to the path for the LAN interface. For this example we are using interface LAN-1.
cd LAN-1
3.3) Use the following command to set the user data for authentication at the RADIUS server:
set credentials <username>:<password>
In this example, the command is set credentials ap1:ap1
3.4) Use the following command to set the authentication method as PEAP/MSCHAPv2:
set Method PEAP/MSCHAPv2
| Info |
|---|
As an alternative, you can use the following script to upload the changes to the access point with LANconfig. Please be sure to add the relevant username and password to the file first. |