| Seiteneigenschaften |
|---|
The Domain Name System (DNS) is one of the fundamental protocols services of the Internet. Without the lookup services it provides, it would be difficult to find anything on the internet. To visit a website, you would need to know the exact IP address of the server hosting it, which is impossible. For this reason, DNS traffic is some of the most trusted data on the internet.Companies , and therefore companies usually allow the DNS protocol to pass bidirectionally through their firewall (both inbound and outbound) because it . This is necessary for their internal employees to visit external sites and for external users to find their websites.so that, for example, employees can call up external websites and customers or prospective customers are able to find the company's websites.
This offers the usual convenience of using the internet, but also opens up opportunities for potential attackers to infect a network.
One way to attack a network via DNS is the method of DNS tunneling. Here, DNS requests are used A network attack using DNS tunneling takes advantage of this fact by using DNS requests to implement a command and control channel for malware. Inbound Incoming DNS traffic can transmit transmits the commands to the malware , while outbound traffic can exfiltrate sensitive data or provide responses to the malware operator's requests. DNS tunneling and outgoing DNS traffic transmits sensitive data and information to the attacker. DNS tunnelling can also be used to bypass circumvent regulations in networks, for example, e.g. by leveraging hotspot logins or blocked services.
This works because DNS is a very flexible protocol. There are very few restrictions on the data a DNS query contains because it is designed to look up domain names of websites. Since almost anything can be a domain name, these fields can be used to transmit sensitive information. These queries are designed to go to attacker-controlled DNS servers so they can receive the queries and respond in the appropriate DNS responses.
Due to the fact that the DNS protocol is very adaptable, such actions are usually successful. The requests are designed to be sent to DNS servers that are controlled by the attackers. Thus, the DNS servers are able to receive the requests and transmit data in corresponding DNS responses.
Since numerous DNS tunneling tools are offered for download on the Internet, DNS tunneling attacks can be carried out quite easily. Even inexperienced attackers are thus able to route data past the security devices of a network or, for example, to bypass the login to a (chargeable) WLAN hotspot without having to authenticate the requesting WLAN DNS tunneling attacks are easy to carry out and there are numerous DNS tunneling toolkits available. This makes it possible even for inexperienced attackers to use this technique to smuggle data past a company's network security solutions (e.g. firewall) or to bypass hotspots, for example, without having to authenticate a client.
As of LCOS 10.50 RC3REL, all DNS queries that pass through the LANCOM DNS forwarder are therefore subjected to a security check. This prevents data tunnels from being transported via DNS messages.
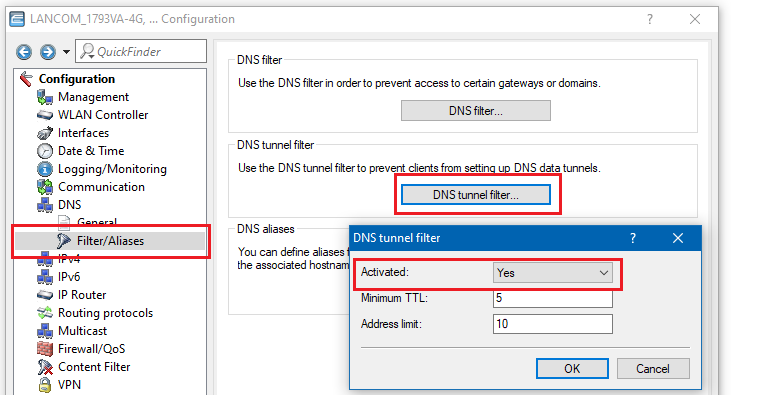
The check is activated by default, but can be deactivated if required in the configuration in the menu DNS → Filter/Aliases → DNS Tunnel Filter. However, we recommend not deactivating the check.
Possible error pattern that can occur when the check is activated:
...
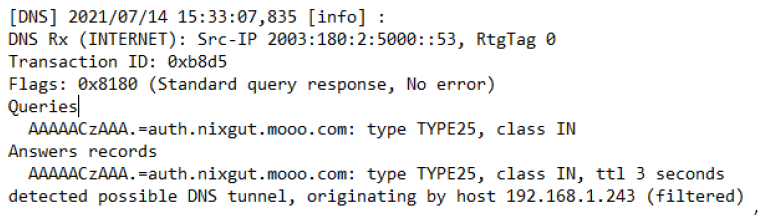
The error pattern can be analysed with a DNS trace on the LANCOM router (see the following figure):
In this case, the following additional entries are written in the syslog of the LANCOM router:
...