...
| Info |
|---|
| This scenario also includes the “parallel” solution as described in this article. |
Procedure:
The setup for scenarios 1 and 2 are basically the same. Scenario 2 additionally requires port forwarding to be set up on the upstream router (see section 4).
In order for the Unified Firewalls in the headquarter as well as in the branch office to be able to accept VPN SSL dial-in connections, a CA and one certficate have to be created on each Unified Firewall. The VPN SSL certificate is used in the VPN SSL settings and serves to decrypt the connections. The certificate is then exported and imported into the other Unified Firewall. The There, the imported certificate is used in the VPN SSL connection and serves to encrypt the connection.
...
2.1.2) Leave the setting on Import Certificate, select the certificate file exported in the branch office in step 1.2.65) and click Import.
| Info |
|---|
Since the Private Key has not been exported no passwords have to be entered. |
...
2.2.2) Leave the setting on Import Certificate, select the certificate file exported in the headquarter in step 1.1.65) and click Import.
| Info |
|---|
Since the Private Key has not been exported no passwords have to be entered. |
...
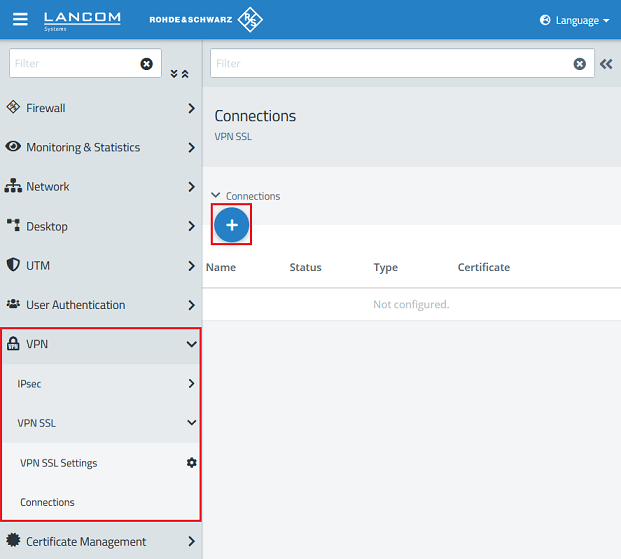
3.1.1) In the headquarter go to the menu VPN → VPN SSL → Connections and click on the "Plus" icon to create a new VPN SSL connection.
3.1.2) Modify the following parameters and click Create:
- Name: Enter a descriptive name (in this example VPN_SSL_Office). Please note, that only letters, numbers and underscores are allowed in the name.
- Certificate: In the dropdown menu select the VPN certificate imported in step 2.1.2.
- Connection type: Select the option Site-To-Site (Server).
- Remote Networks: Add Enter the local network of the branch office in CIDR notation and add it via the "Plus" icon (in this example 192.168.24.0/24).
| Info |
|---|
If additional networks should be reachable from the Office via the Headquarter (e.g. via a separate VPN connection), these networks have to be entered as Additional Local Networks. The configuration is pushed from the Headquarter (Server) to the Office (Client), which creates routing entries for the transmitted networks. |
3.1.3) Click on the button to create a VPN network.
3.1.4) Modify the following parameters and click Create:
- Name : Enter a descriptive name (in this example VPN-SSL-Office).
- Connection Type : Select the option VPN-SSL .
- VPN-SSL Connection : In the dropdown menu select the VPN connection created in step 3.1.2 .
3.1.5) On the desktop click on the VPN network created in step 3.1.4, select the "connection tool" and click on the network object the site-to-site connection should have access to.
3.1.6) Click on the "Plus" icons to assign the necessary protocols to the connection.
| Info |
|---|
| A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication. |
3.1.7) Finally, implement the configuration changes by clicking Activate in the Unified Firewall. This concludes the configuration steps on the Unified Firewall in the headquarter.
...
3.2.1) In the headquarter go to the menu VPN → VPN SSL → Connections and click on the "Plus" icon to create a new VPN SSL connection.
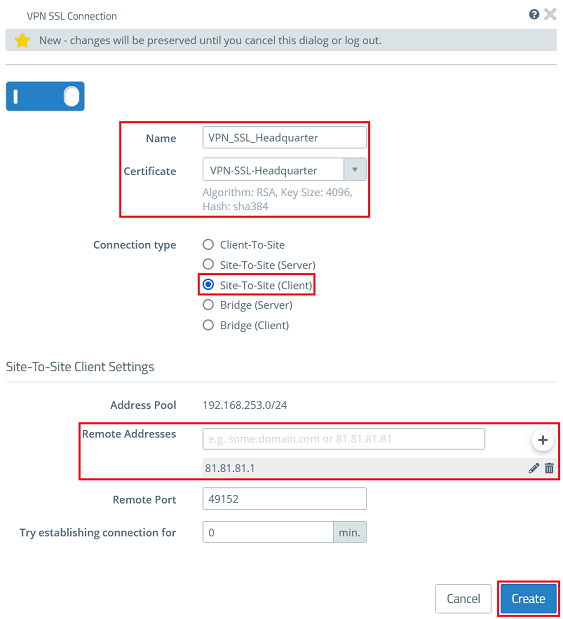
3.2.2) Modify the following parameters and click Create:
- Name: Enter a descriptive name (in this example VPN_SSL_Headquarter). Please note, that only letters, numbers and underscores are allowed in the name.
- Certificate: In the dropdown menu select the VPN certificate imported in step 2.2.2.
- Connection type: Select the option Site-To-Site (Client).
- Remote Addresses: Enter the public IP address or the DNS name of the Unified Firewall or the router in the headquarter and addit via the "Plus" icon.
3.2.3) Click on the button to create a VPN network.
3.2.4) Modify the following parameters and click Create:
- Name : Enter a descriptive name (in this example VPN-SSL-Headquarter).
- Connection Type : Select the option VPN-SSL .
- VPN-SSL Connection : In the dropdown menu select the VPN connection created in step 3.2.2 .
3.2.5) On the desktop click on the VPN network created in step 3.2.4, select the "connection tool" and click on the network object the site-to-site connection should have access to.
3.12.6 Click on the "Plus" icons to assign the necessary protocols to the connection.
| Info |
|---|
| A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication. |
3.12.7 Finally, implement the configuration changes by clicking Activate in the Unified Firewall. This concludes the configuration steps on the Unified Firewall in the branch office.
...
- First port : Specify the p ort 49152 .
- Last port : Specify the p ort 49152 .
- Intranet address : Specify the IP address of the Unified Firewall in the transfer network between the Unified Firewall and the LANCOM router.
- Protocol : In the dropdown menu select the option UDP .
4.3) Write the configuration back to the router.
...
| Forms | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||
Thank you for your feedback! You can also send us constructive suggestions for improving our knowledge base or ideas for new articles by email to knoweldgebase@lancom.de. |