Description: This document describes how you can control the registration of a SIP terminal (SIP telephone, SIP PBX, etc.) at the provider by using the layer-7 application control. This procedure is suitable for load-balancer scenarios where the SIP terminal should always use the same Internet connection to register with the provider. Requirements:The LANCOM router must operate as a DNS server or DNS forwarder in the network. Clients on the local network must use the router as a DNS server. In addition, clients need to be prevented from using DNS-over-TLS and DNS-over-HTTPS (also in the browser) directly with external DNS servers. This can be achieved with the following options:- The DHCP server has to communicate the IP address of the router as a DNS server. The Internet Setup Wizard configures this by default.
- Firewall rules have to be set up to prevent the direct use of external DNS servers, e.g. by blocking the outgoing port 53 for clients on the source network.
- Firewall rules have to be set up that prevent the direct use of external DNS servers that support DNS-over-TLS, e.g. by blocking the outgoing port 853 for clients on the source network.
- Disable DNS-over-HTTPS (DoH) in the browser.
Notes on how to synchronize the firewall's DNS database:Since the firewall learns its information from the DNS requests of the clients, in certain situations the DNS database will be incomplete. This can happen in the following situations: - A new firewall rule is added, but the client still has a cached DNS entry.
- The router was restarted when the client already has a cached DNS entry.
Helpful in these cases is emptying the DNS cache on the client, rebooting the client, or a time-out of the DNS record on the client. The router’s own services, such as ping, are not handled by the firewall rules. By sending a ping to a full DNS name (without wildcard expressions), the generation of rule resolutions (DNS to IP addresses) can be performed on-demand either from the command line (once) or by a cron job.
Note:
Different DNS names that resolve to the same IP address cannot be distinguished. In this case, the first rule that references one of these DNS names will apply. That should not be a problem for large service providers. However, it could occur with small websites hosted by the same vendor.
Example scenario: This example is for configuring the following scenario: - Two Internet connections and a load balancer are available:
- LOADBLANCER with routing tag 0
- INTERNET with routing tag 1 and
- INTERNET2 with routing tag 2
How to configure a scenario like this is described in the following Knowledge Base article 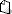 . 
- A SIP terminal should always log in to the SIP provider SIPGATE (sipgate.de) via Internet connection INTERNET2 and all calls should be made via this Internet connection.
Procedure:1) In order to reference DNS destinations in firewall rules, the destinations first have to be configured in the menu Firewall/QoS → General → DNS destination. Create a new entry for your SIP provider. Here you enter the URL that your SIP provider gave to you for the registration. 2) Open the menu Firewall/QoS → IPv4 rules → Rules and add a new firewall rule. 3) Enter a descriptive name for the new rule. 4) Set the item Routing tag to the value 2, so that the SIP terminal registers and communicates over the default route with the routing tag 2 (remote site Internet2). 5) Click Add to add the ACCEPT object. 7) Switch to the Stations tab and, under Connection source, enter (for example) the IP address of the SIP terminal and set the Connection destination to the DNS destination SIPGATE. 8) On the Services tab you can either allow all services for the SIP terminal communication with the SIP provider or allow only those ports that are used for communication with the SIP provider (see the figure “Optional”). Optional:
The ports used for SIP communication differ depending on the provider. Please be sure to obtain the relevant information from your SIP provider in advance.
9) Save the firewall rule by clicking OK and write the configuration back to the router.
Info:
For application-based routing, there is the new parameter FW-DNS for the trace command. It can monitor changes to the firewall database of DNS destinations: - If a DNS packet arrives, it outputs the packet along with the affected wildcard expressions and destinations.
- If the TTL (time-to-live) of an entry expires, it outputs the associated record along with the relevant wildcard expressions and destinations.
- If one of the two firewalls registers or de-registers a DNS destination because its configuration has changed.
- If there is a change to the tables Setup -> Firewall -> DNS-Destinations or Setup -> Firewall -> DNS-Destination-List.
|