
Description:
This document describes how to set up a VPN-SSL connection (site-to-site) between two LANCOM R&S®Unified Firewalls (referred to in the following as Unified Firewalls).
Requirements:
| Please ensure that the address ranges of the local networks being connected via VPN do not overlap with the default networks configured on the Unified Firewall ports (e.g. 192.168.2.0/24, 192.168.3.0/24)! |
Scenario:
1) The Unified Firewall is connected directly to the Internet and has a public IPv4 address:
A company wants to use a VPN-SSL connection to connect their Unified Firewall at the headquarters to their Unified Firewall at the branch office.
Headquarter:
Branch office:

A company wants to use a VPN-SSL connection to connect their Unified Firewall at the headquarters to their Unified Firewall at the branch office.
Headquarter:
Branch office:
| This scenario also includes the “parallel” solution as described in this article. |

Procedure:
The setup for scenarios 1 and 2 are basically the same. Scenario 2 additionally requires port forwarding to be set up on the upstream router (see section 4).
In order for the Unified Firewalls in the headquarter as well as in the branch office to be able to accept VPN SSL dial-in connections, a CA and one certficate have to be created on each Unified Firewall. The VPN SSL certificate is used in the VPN SSL settings and serves to decrypt the connections. The certificate is then exported and imported into the other Unified Firewall. The imported certificate is used in the VPN SSL connection and serves to encrypt the connection.
1) Creating certificates and modifying the VPN SSL settings:
1.1) Creating certificates and modifying the VPN SSL settings on the Unified Firewall in the headquarter:
1.1.1) Connect to the Unified Firewall in the headquarter, switch to the menu Certificate Management → Certificates and click on the "Plus" icon to create a new certificate.

1.1.2) Modify the following parameters to create a CA and click Create:

1.1.3) Create another certificate by clicking on the "Plus" icon. In step 1.1.4 it is exported and entered in the VPN SSL settings in the headquarter afterwards (see step 1.1.8). For this purpose modify the following parameters and click Create:

1.1.4) For the certificate created in step 1.1.3 click on the icon for the certificate export.

1.1.6) Select the format PEM / CRT, activate the option Export Certificate Chain and click Export.

1.1.7) Switch to the menu VPN → VPN SSL → VPN SSL Settings.

1.1.8) Activate the VPN SSL service via the slider, modify the following parameters and click Save:
If necessary, you can change the Protocol and the Port. The Adress Pool is the range of IP addresses that are assigned to the dial-in VPN SSL clients. This address range may not already be in use as an internal network in the Unified Firewall. |

1.2) Creating certificates and modifying the VPN SSL settings on the Unified Firewall in the branch office:
1.2.1) Connect to the Unified Firewall in the branch office, switch to the menu Certificate Management → Certificates and ckick on the "Plus" icon to create a new certificate.

1.2.2) Modify the following parameters to create a CA and click Create:

1.2.3) Create another certificate by clicking on the "Plus" icon. This is used in the VPN SSL settings in the branch office (see step 1.2.8). For this purpose modify the following parameters and click Create:

1.2.4) For the certificate created in step 1.2.3 click on the icon for the certificate export.

1.2.5) Select the format PEM / CRT, activate the option Export Certificate Chain and click Export.

1.2.6) Switch to the menu VPN → VPN SSL → VPN SSL Settings.

1.2.7) Activate the VPN SSL service via the slider, modify the following parameters and click Save:
| If necessary, you can change the Protocol and the Port. The Adress Pool is the range of IP addresses that are assigned to the dial-in VPN SSL clients. This address range may not already be in use as an internal network in the Unified Firewall. |

2) Importing the certificates:
2.1) Importing the VPN SSL certificate on the Unified Firewall in the headquarter:
2.1.1) On the Unified Firewall in the headquarter go to the menu Certificate Management → Certificates and click on the button for the certificate import.

2.1.2) Leave the setting on Import Certificate, select the certificate file exported in the branch office in step 1.2.6) and click Import.
Since the Private Key has not been exported no passwords have to be entered. |

2.2) Importing the VPN SSL certificate on the Unified Firewall in the branch office:
2.2.1) On the Unified Firewall in the branch office go to the menu Certificate Management → Certificates and click on the button for the certificate import.

2.2.2) Leave the setting on Import Certificate, select the certificate file exported in the headquarter in step 1.1.6) and click Import.
Since the Private Key has not been exported no passwords have to be entered. |

3) Setting up the VPN SSL connections and the firewall rules:
3.1) Setting up the VPN SSL connection and the firewall rule on the Unified Firewall in the headquarter:
3.1.1) In the headquarter go to the menu VPN → VPN SSL → Connections and click on the "Plus" icon to create a new VPN SSL connection.
3.1.2) Modify the following parameters and click Create:
If additional networks should be reachable from the Office via the Headquarter (e.g. via a separate VPN connection), these networks have to be entered as Additional Local Networks. The configuration is pushed from the Headquarter (Server) to the Office (Client), which creates routing entries for the transmitted networks. |

3.1.3) Click on the button to create a VPN network.

3.1.4) Modify the following parameters and click Create:

3.1.5) On the desktop click on the VPN network created in step 3.1.4, select the "connection tool" and click on the network object the site-to-site connection should have access to.

3.1.6) Click on the "Plus" icons to assign the necessary protocols to the connection.
| A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication. |


3.1.7) Finally, implement the configuration changes by clicking Activate in the Unified Firewall. This concludes the configuration steps on the Unified Firewall in the headquarter.

3.2) Setting up the VPN SSL connection and the firewall rule on the Unified Firewall in the branch office:
3.2.1) In the headquarter go to the menu VPN → VPN SSL → Connections and click on the "Plus" icon to create a new VPN SSL connection.

3.2.2) Modify the following parameters and click Create:
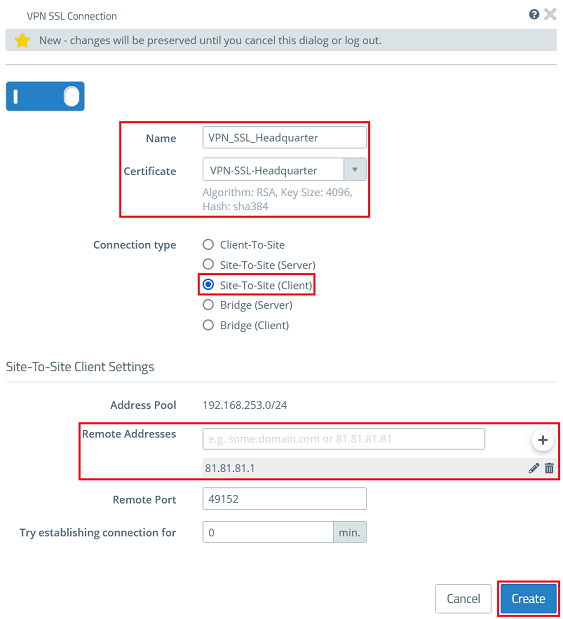
3.2.3) Click on the button to create a VPN network.

3.2.4) Modify the following parameters and click Create:

3.2.5) On the desktop click on the VPN network created in step 3.2.4, select the "connection tool" and click on the network object the site-to-site connection should have access to.

3.1.6 Click on the "Plus" icons to assign the necessary protocols to the connection.
| A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication. |


3.1.7 Finally, implement the configuration changes by clicking Activate in the Unified Firewall. This concludes the configuration steps on the Unified Firewall in the branch office.

4) Setting up port forwarding on the LANCOM router (scenario 2 only):
Site-to-site VPN SSL uses the UDP port 49152 by default. It must be forwarded to the Unified Firewall.
The port for VPN SSL can be changed in the Unified Firewall. If you are using a router from another manufacturer, approach them for information about the appropriate procedure. |
4.1) Open the configuration of the router in LANconfig and got to the menu IP Router → Masq. → Port forwarding table.

4.2) Modify the following parameters:

4.3) Write the configuration back to the router.