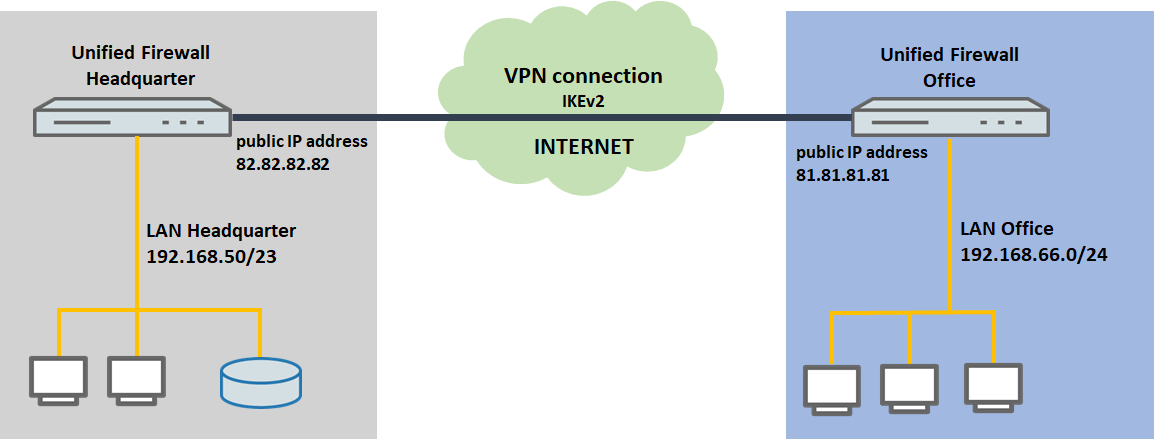
Description:
This document describes how to set up an IKEv2 connection (site-to-site) between two LANCOM R&S®Unified Firewalls.
Requirements:
Scenario:
The Unified Firewalls are connected directly to the Internet and have a public IPv4 address:
Info:
If the Unified Firewall uses an upstream (LANCOM) router to connect to the Internet, then the upstream device has to be set to forward its inbound ports 4500 and 500 to the LAN IP address of the Unified Firewall.

Procedure:
1) Configuration steps on the Unified Firewall at the headquarters:
1.1) Connect to the configuration interface of the Unified Firewall and navigate to VPN -> IPSec -> IPSec Settings.
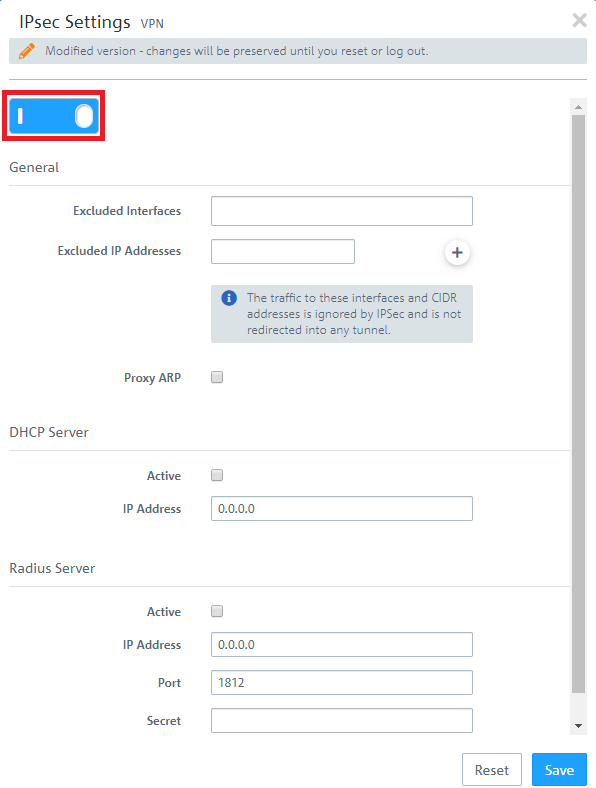
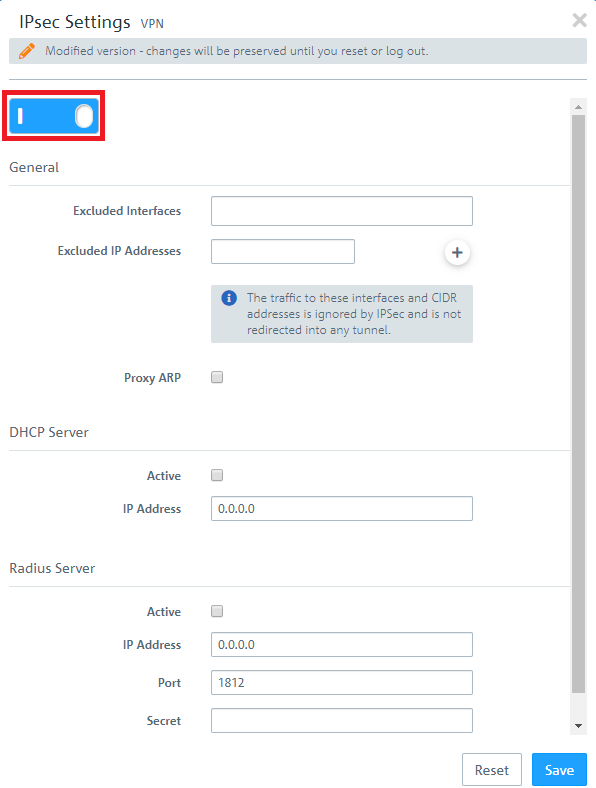
1.2) Activate IPSec.
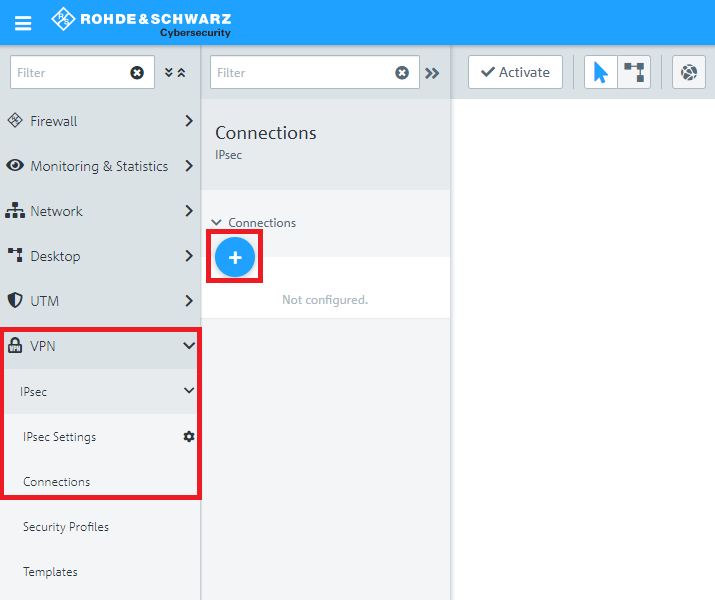
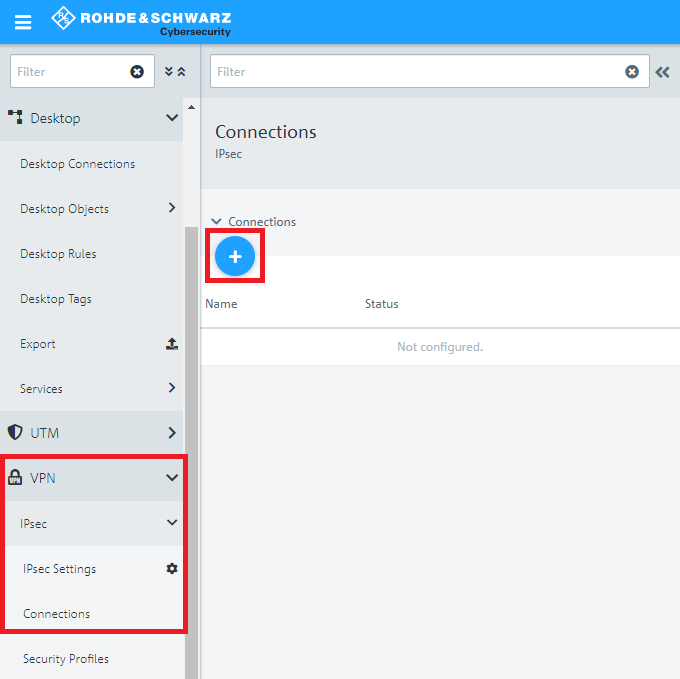
1.3) Switch to VPN -> IPSec -> Connections and click on the “+” icon to create a new IPSec connection.
1.4) Save the following parameters:
If you have created your own template or security profile, you can use these here.

1.5) Change to the Tunnels tab and enter the following parameters:

1.6) Change to the Authentication tab and enter the following parameters:
Important:
The local and remote identifiers must not match!

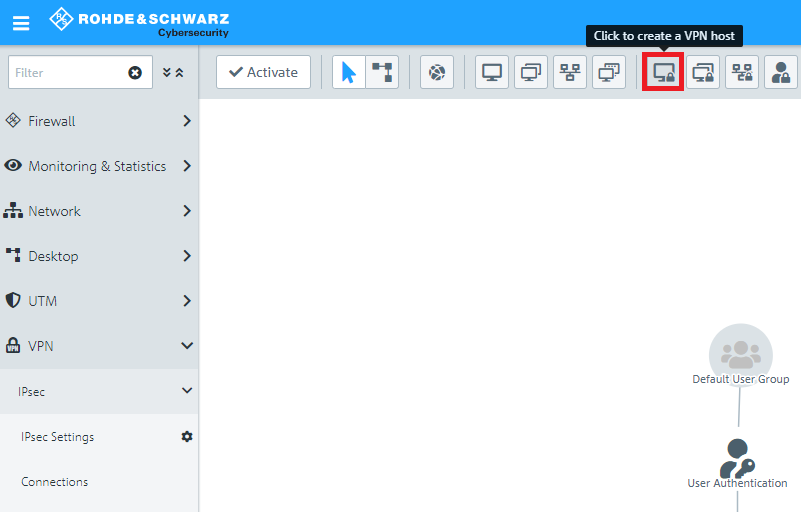
1.7) Click the icon to create a new VPN host.
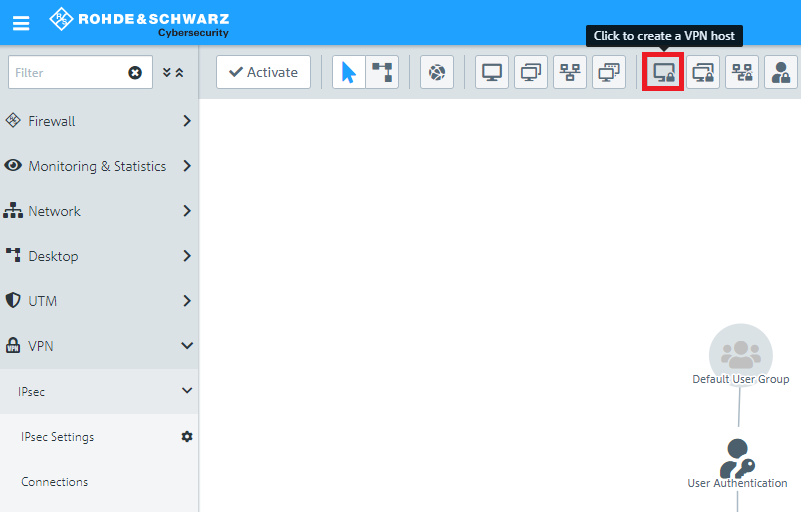
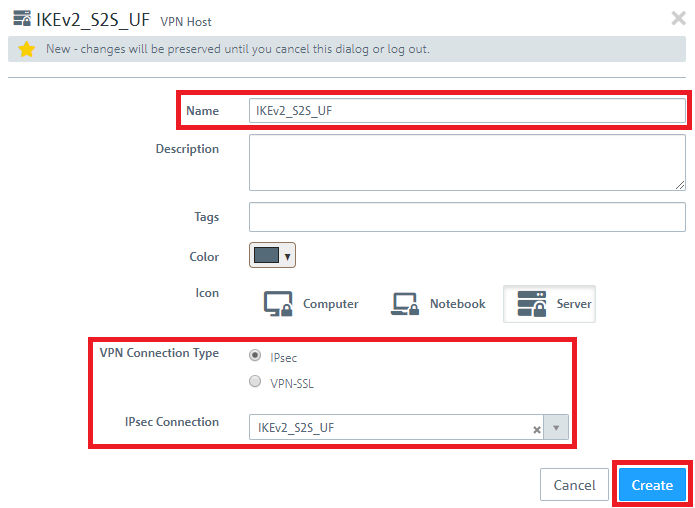
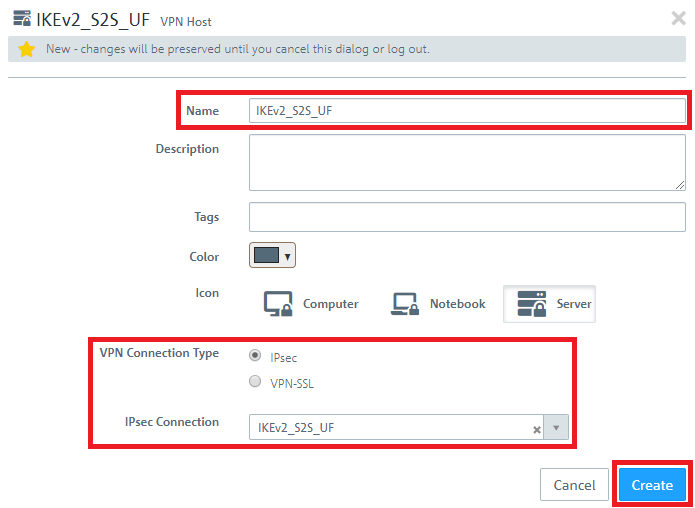
1.8) Save the following parameters:
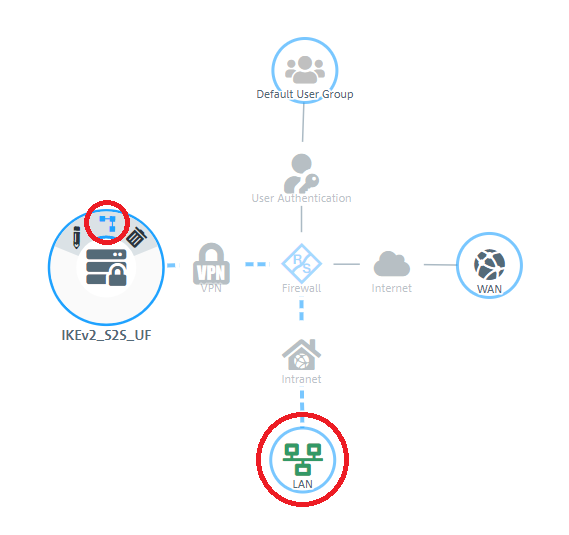
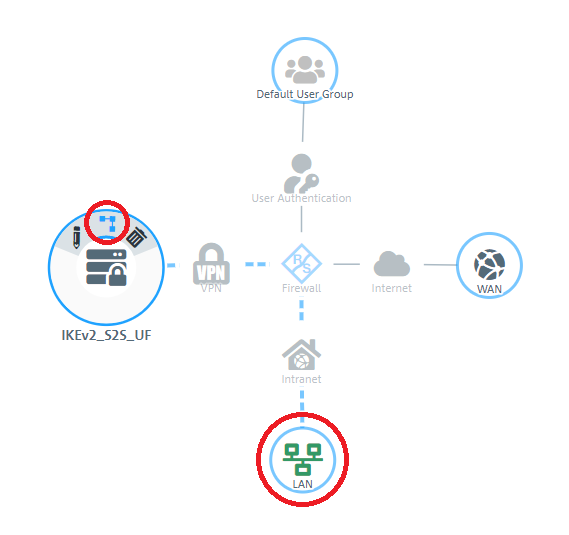
1.9) In the VPN host click on the "connection" icon and, to open the firewall objects, click on the network object that the object (the site-to-site connection) should access. Repeat this step for every network that the branch should be able to access.
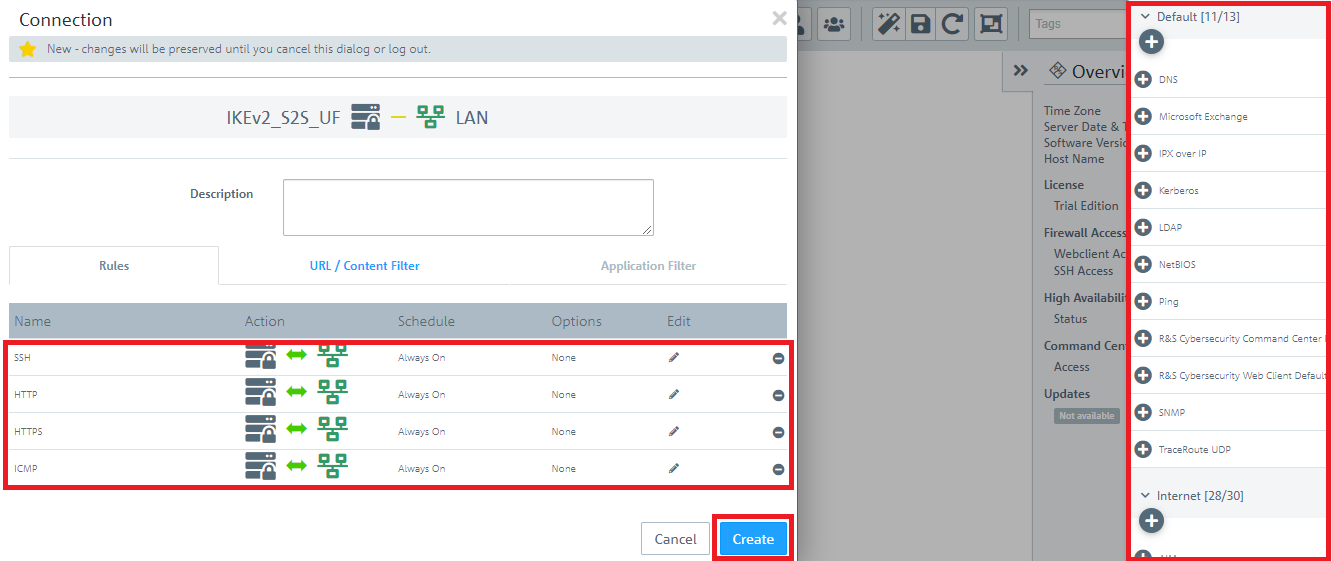
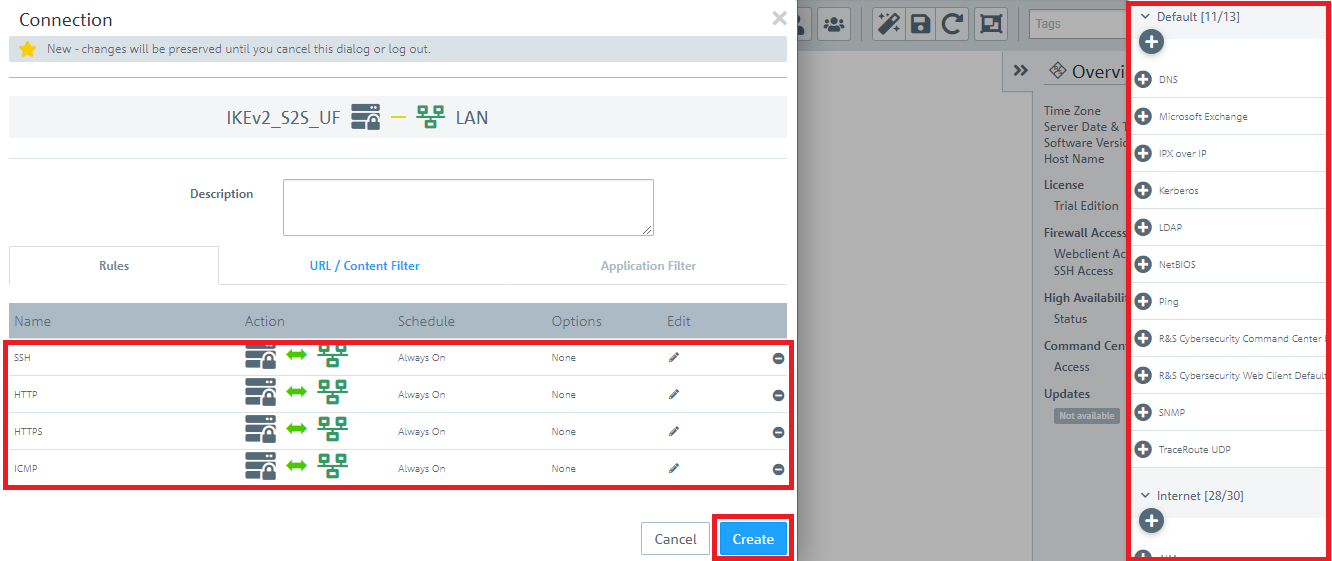
1.10) Use the “+” sign to assign the required protocols to the VPN host.
Info:
A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication.
Info:
Firewall objects can also be accessed via Desktop -> Desktop Connections and clicking on the “edit” icon.
1.11) Finally, implement the configuration changes by clicking Activate in the firewall.
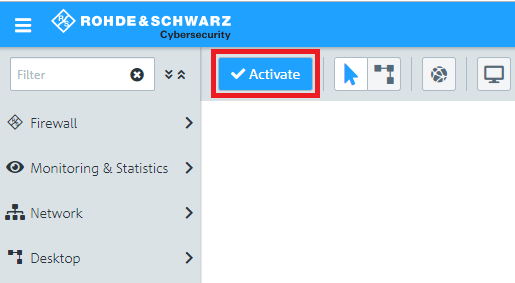
1.12) This concludes the configuration steps on the Unified Firewall at the headquarters.
2) Configuration steps on the Unified Firewall at the branch office:
2.1) Connect to the configuration interface of the Unified Firewall and navigate to VPN -> IPSec -> IPSec Settings.
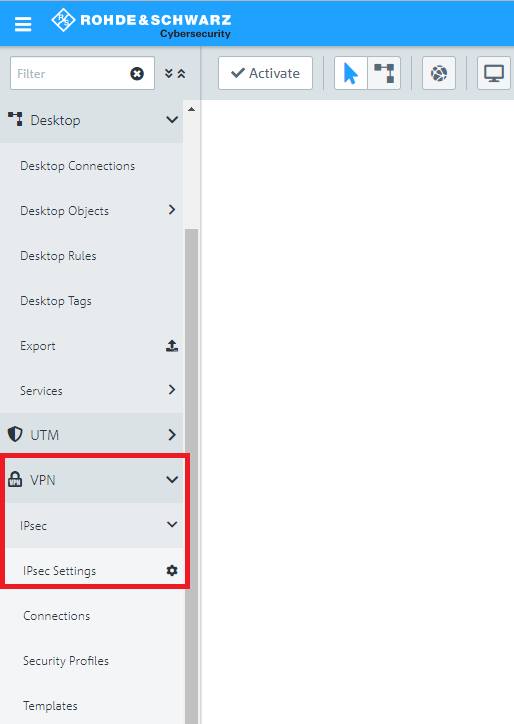
2.2) Activate IPSec.
2.3) Switch to VPN -> IPSec -> Connections and click on the “+” icon to create a new IPSec connection.
2.4) Save the following parameters:
If you have created your own template or security profile, you can use these here.

2.5) Change to the Tunnels tab and enter the following parameters:

1.6) Change to the Authentication tab and enter the following parameters:
Important:
The local and remote identifiers must not match!

2.7) Click the icon to create a new VPN host.
2.8) Save the following parameters:
2.9) In the VPN host click on the "connection" icon and, to open the firewall objects, click on the network object that the object (the site-to-site connection) should access. Repeat this step for every network that the branch should be able to access.
2.10) Use the “+” sign to assign the required protocols to the VPN host.
Info:
A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication.
Info:
Firewall objects can also be accessed via Desktop -> Desktop Connection and clicking on the “edit” icon.
2.11) Finally, implement the configuration changes by clicking Activate in the firewall.
2.12) This concludes the configuration steps on the Unified Firewall at the branch office.
The VPN connection to the headquarters is established now.