Description:
In some environments it is impossible to establish a secure VPN connection over an existing Internet connection due to an interim firewall that blocks the ports used by IPsec. To be able to set up an IPsec-secured VPN connection in such a situation, LANCOM VPN routers and the LANCOM Advanced VPN Client support IPsec-over-HTTPS technology.
Requirements:
- LCOS as of version 8.0 or later (download latest version)
- LANtools as of version 8.0 or later (download latest version)
- For client connections, the Advanced VPN Client version 3 or later (download latest version)
How it works:
With IPsec over HTTPS, an attempt is first made to transfer data using standard IPsec. If the connection cannot be established (e.g. because IKE port 500 is blocked by a cellular network) an attempt is then automatically made to establish a connection that encapsulates the IPsec VPN using an additional SSL header (port 443, like https).
- Due to the multiple encapsulation of the IP packets, data throughput may be reduced.
- IPsec-over-HTTPS technology can only be used when the local and remote devices support this function and when the appropriate options are activated.
Configuration:
IKEv1 connections:
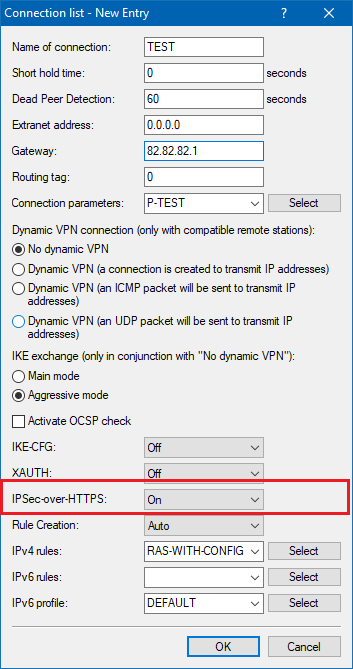
For the active establishment of a connection from one LANCOM VPN router to another VPN remote device using IPsec-over-HTTPS technology, activate the option in the VPN connection name list entry that corresponds to the remote site.
Please note that when the IPsec-over-HTTPS option is activated, the VPN connection can only be established when the remote site also supports this technology and when the remote site is set up to receive passive VPN connections that use IPsec over HTTPS.
Activating this options means that no attempt will be made to establish a connection using UDP (DynVPN).
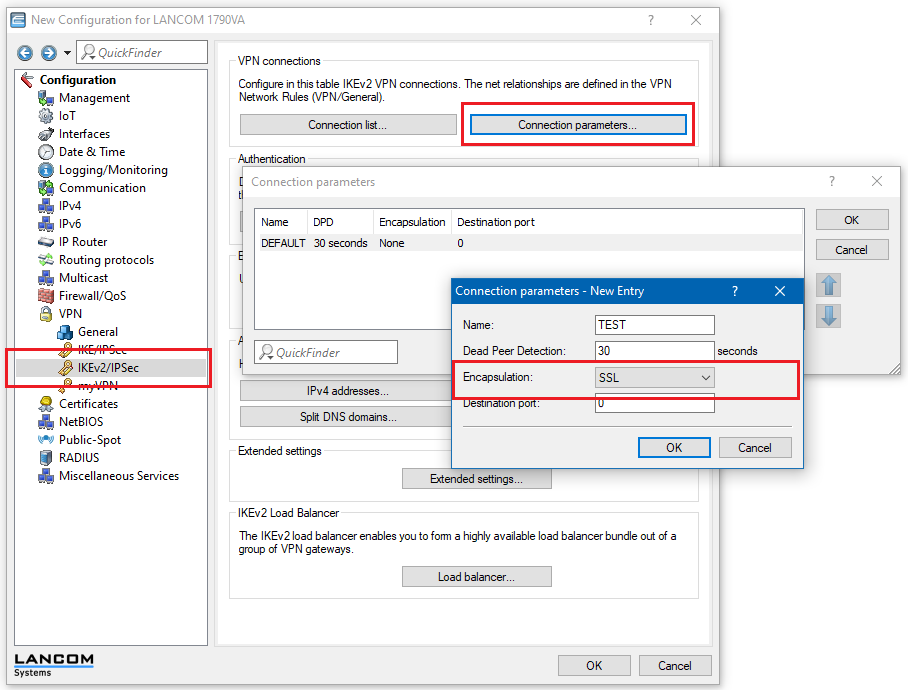
IKEv2 connections:
Open the Connection parameters in the VPN → IKEv2/IPSec menu and create a profile in which you select the "SSL" option as "Encapsulation".
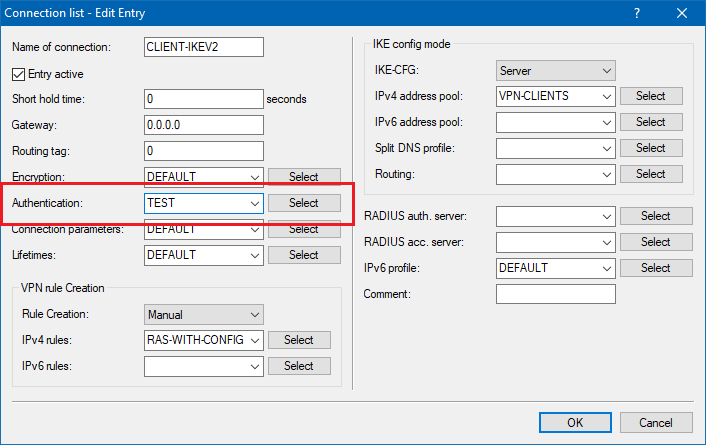
Assign this connection profile to the VPN connections for which you want to use IPSec-over-HTTPS.
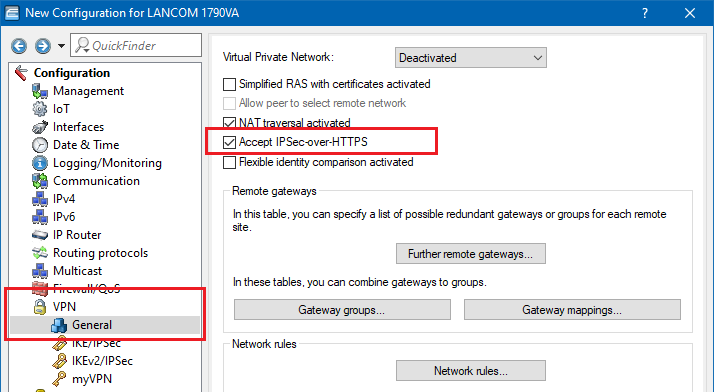
Activate the option Accept IPSec-over-HTTPS in the menu VPN → General to enable passive connection establishment to a LANCOM VPN router from another VPN remote device using IPsec-over-HTTPS technology (LANCOM VPN router or LANCOM Advanced VPN client).
LANCOM Advanced VPN Client:
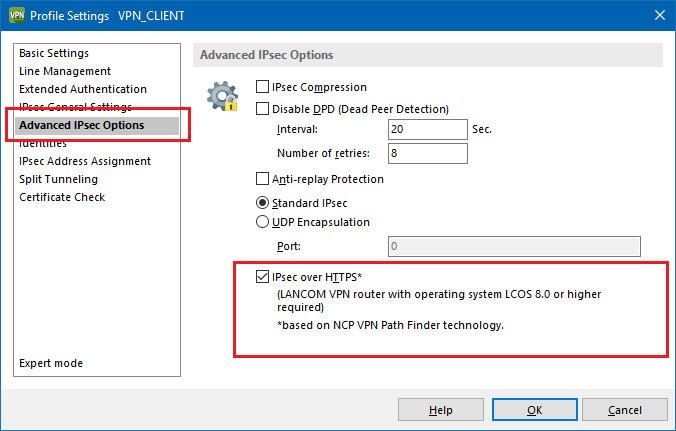
You can activate the IPsec-over-HTTPS function in profile settings under Configuration → Profiles.
- In the profile settings, select Advanced IPsec Options and activate the option IPSec over HTTPS.
Force IPsec over HTTPs in Advanced VPN Client:
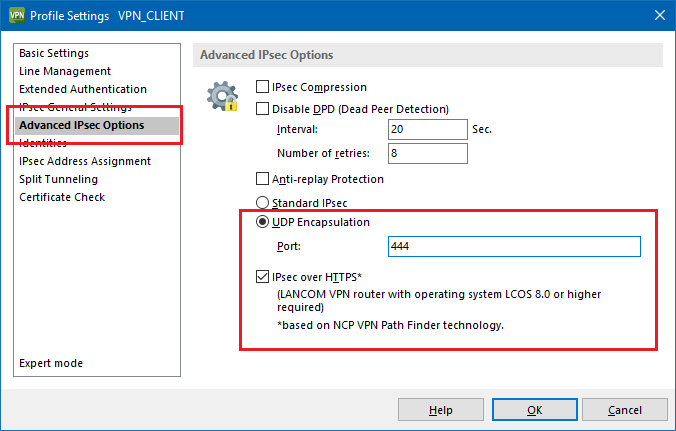
If it is required that the Advanced VPN Client always has to connect via IPsec over HTTPS please do the following:
- Click on your profile, under Advanced IPsec options, set UDP Encapsulation and set the port to a value of 444.
If the option IPSec over HTTPS is active, the LANCOM Advanced VPN Client automatically performs a fallback to IPsec over HTTPS when the mode Standard IPSec is used. With this setting, the VPN client will first attempt to establish a connection without using additional SSL encapsulation. If this connection cannot be established, the device will then establish a connection with additional SSL encapsulation.