Description:
This document describes how to set up a certificate-based IKEv2 (site-to-site) connection between a LANCOM router and a LANCOM R&S®Unified firewall.
The certificate module was updated in LCOS FX 10.7, therefore the corresponding menus differ compared to older LCOS FX versions. The configuration of a certificate-based IKEv2 connection between a LANCOM router and a Unified Firewall is described in the following article:
Requirements:
- LANCOM R&S Unified Firewall as of LCOS FX 10.4 and up to and including LCOS FX 10.6
- LANCOM VPN router
- LCOS as of version 10.20 (download)
- LANtools from version 10.20 (download)
- A configured and functional Internet connection on the Unified Firewall
- Web browser for configuring the Unified Firewall.
The following browsers are supported:
- Google Chrome
- Chromium
- Mozilla Firefox
Scenario:
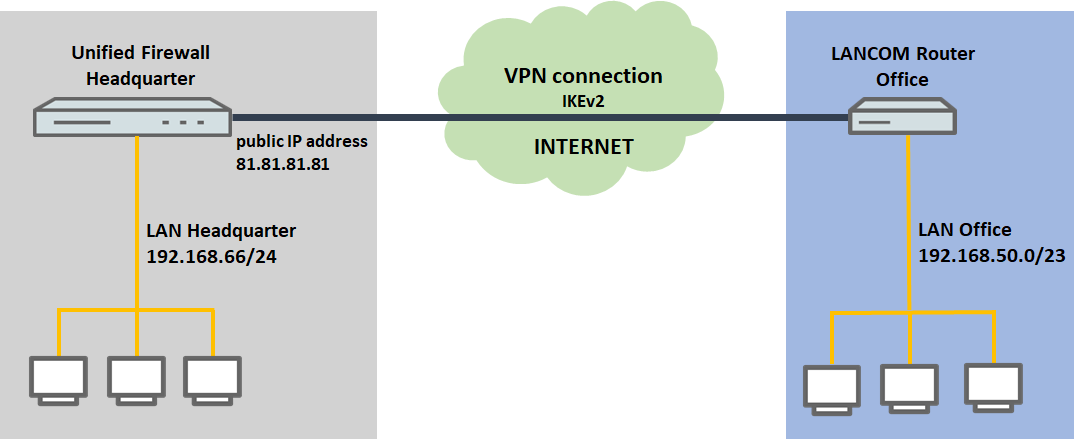
1) The Unified Firewall is connected directly to the Internet and has a public IPv4 address:
- A company wants to use an IKEv2 site-to-site connection to connect its branch office, where a LANCOM router operates as an Internet gateway, to its company headquarters.
- The company headquarters has a Unified Firewall as a gateway with an Internet connection with the fixed public IP address 81.81.81.81.
- The LANCOM router at the branch office should establish the VPN connection to the headquarters.
- The local network at the headquarters has the IP address range 192.168.66.0/24.
- The local network at the branch office has the IP address range 192.168.50.0/23.
- The VPN connection should be authenticated using certificates. The CA of the Unified Firewall is used.
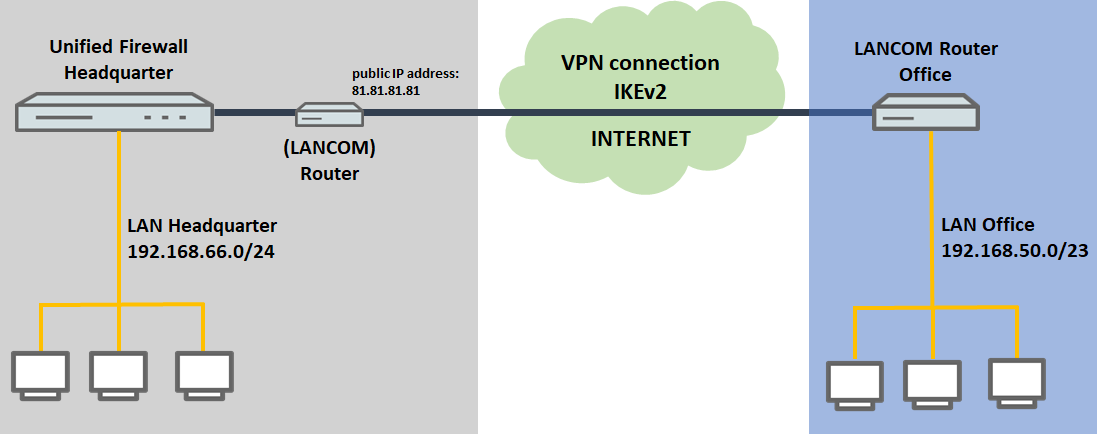
2) The Unified Firewall is connected to the Internet via an upstream router:
- A company wants to use an IKEv2 site-to-site connection to connect its company headquarters to a branch office, where a LANCOM router operates as an Internet gateway.
- The company headquarters has a Unified Firewall as the gateway and an upstream router for the Internet connection. The router has the fixed public IP address 81.81.81.81.
- The LANCOM router at the branch office should establish the VPN connection to the headquarters.
- The local network at the headquarters has the IP address range 192.168.66.0/24.
- The local network at the branch office has the IP address range 192.168.50.0/23.
- The VPN connection should be authenticated using certificates. The CA of the Unified Firewall is used.
Procedure:
The setup for scenarios 1 and 2 are basically the same. Scenario 2 additionally requires port and protocol forwarding to be set up on the upstream router (see section 5).
1) Creating the CA and VPN certificates on the Unified Firewall:
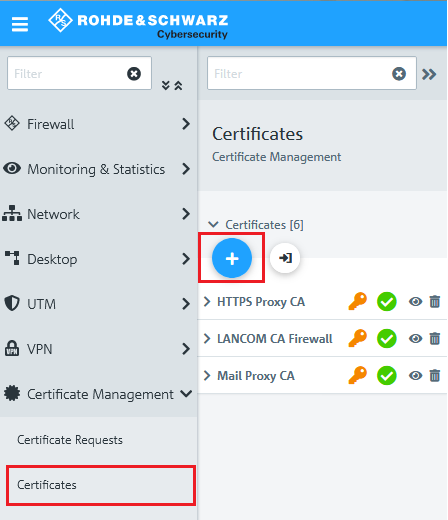
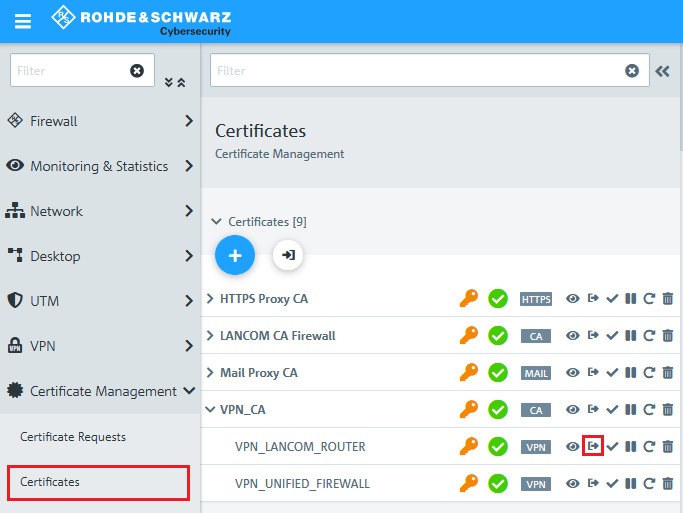
1.1) Connect to the configuration interface of the Unified Firewall, go to the menu Certificate Management → Certificates and click on the "+" icon to create a new routing entry.
1.2) The first step is to create a Certification Authority (CA) for VPN connections.
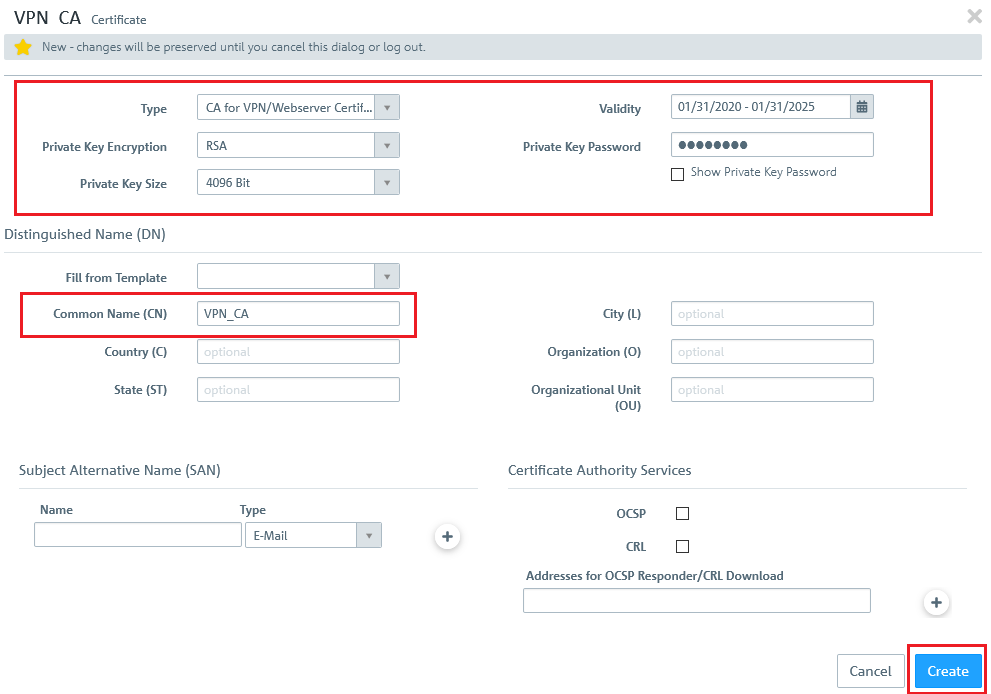
- In the drop-down menu "Type" of the window displayed at top left, select the option "CA for VPN/Webserver certificates".
- In the field "Private key size", select the value 4096 bit.
- Enter a common name of your choice.
- Set a Validity period.
- Set any Private Key Password.
1.3) Then click the Create button.
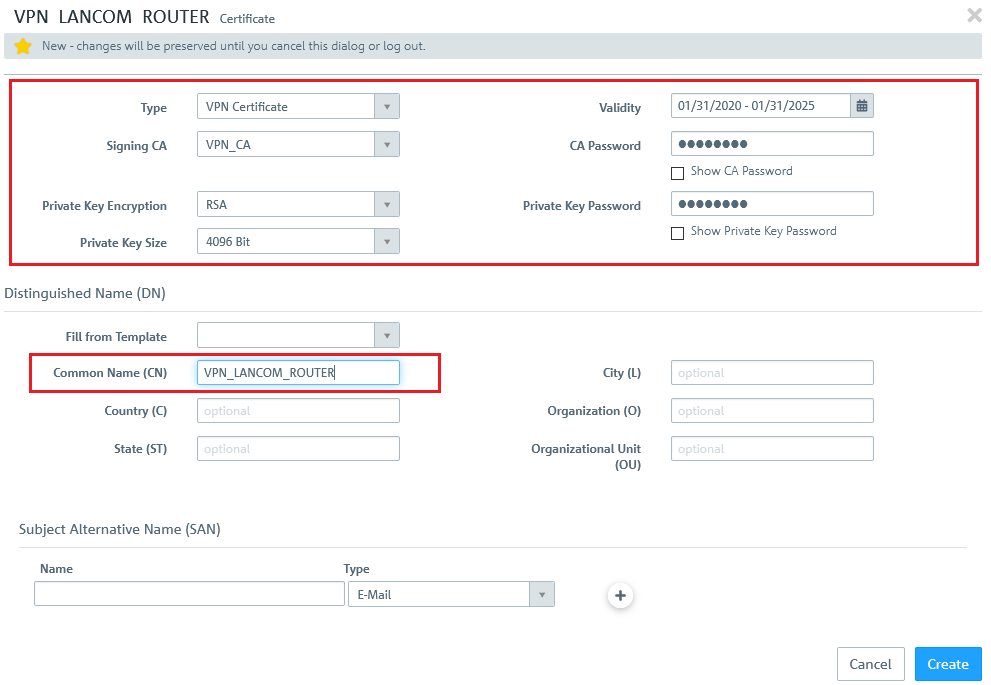
1.4) Click on the "+" icon to create a certificate for the LANCOM router at the branch office:
- In the drop-down menu "Type" of the window displayed at top left, select the option "VPN certificate".
- Set the "Signing CA" to the VPN_CA from step 1.2.
- In the field "Private key size", select the value 4096 bit.
- Enter a common name of your choice.
- Set a Validity period.
- In the field CA Password enter the password set in step 1.2.
- Assign any private key password.
1.5) Then click the Create button.
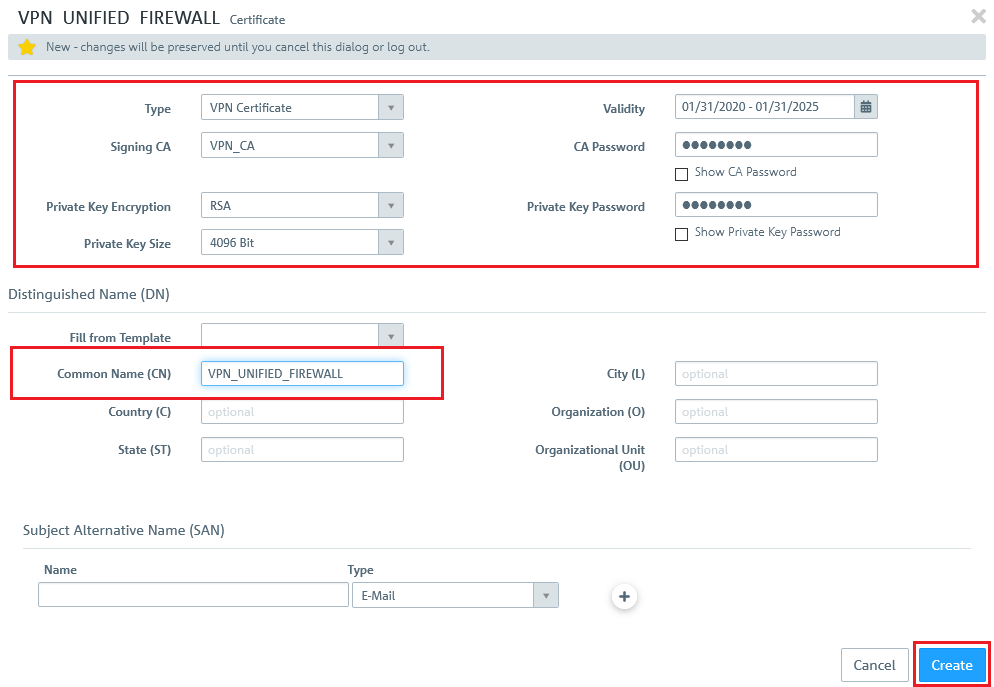
1.6) Click on the "+" icon to create a VPN certificate for the United Firewall at the headquarter:
- In the drop-down menu "Type" of the window displayed at top left, select the option "VPN certificate".
- Set the "Signing CA" to the VPN_CA from step 1.2.
- In the field "Private key size", select the value 4096 bit.
- Enter a common name of your choice.
- Set a Validity period.
- In the field CA Password enter the password set in step 1.2.
- Assign any private key password.
1.7) Then click the Create button.
2) Creating the VPN connection on the Unified Firewall:
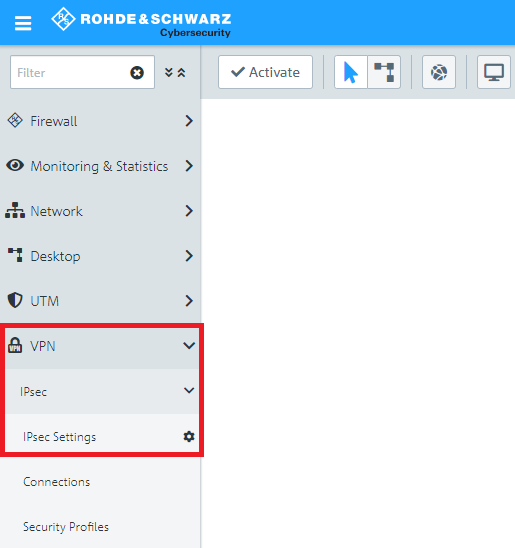
2.1) Navigate to the menu VPN → IPsec settings.
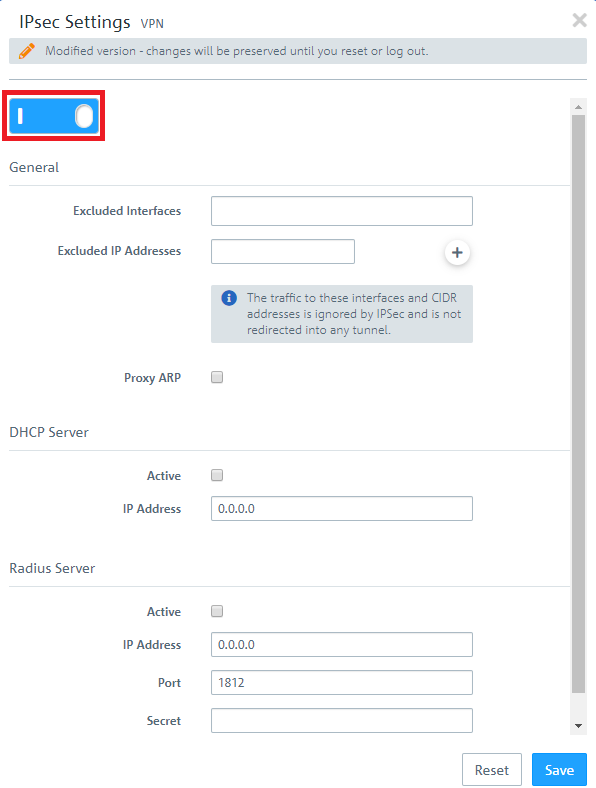
2.2) Activate IPsec.
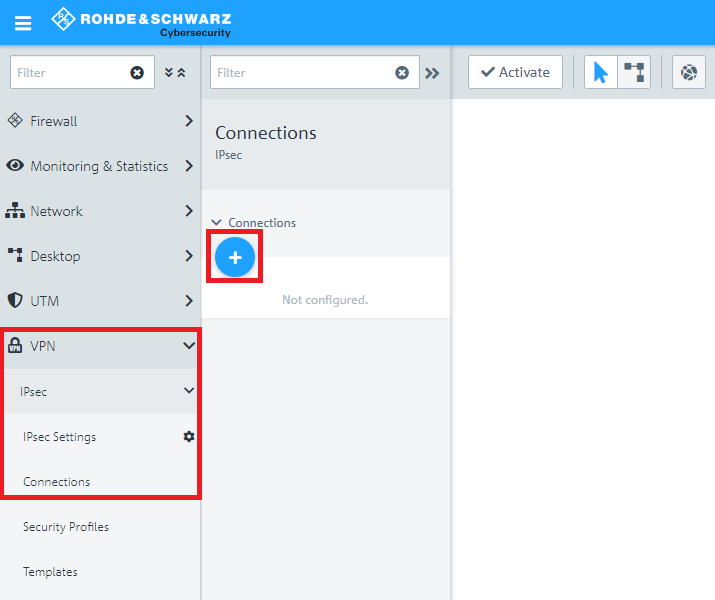
2.3) Switch to VPN → IPsec Connections and click on the "+" icon to create a new IPsec connection.
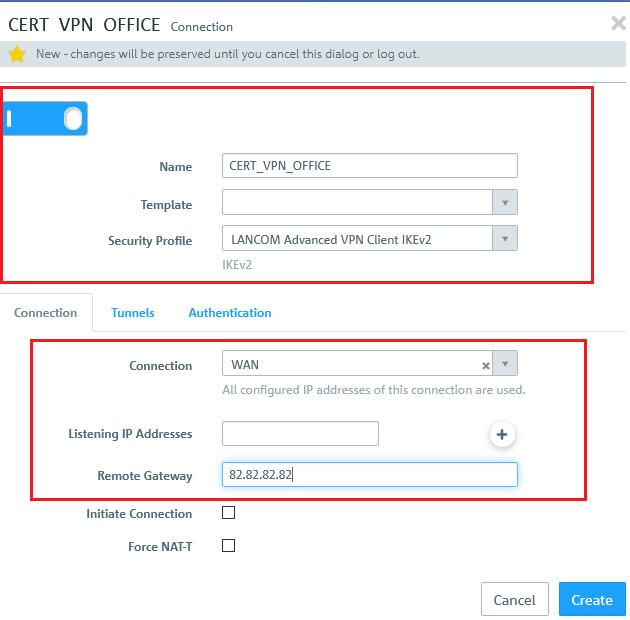
2.4) Save the following parameters:
- Name: Enter a descriptive name.
- Security profile: Select the profile LANCOM LCOS Default IKEv2.
- Connection: From the drop-down menu, select the Network connection used for the Internet connection.
- Remote Gateway: Enter the public IP or DNS address of the LANCOM router at the branch office.
If you have created your own template or security profile, you can use these here.
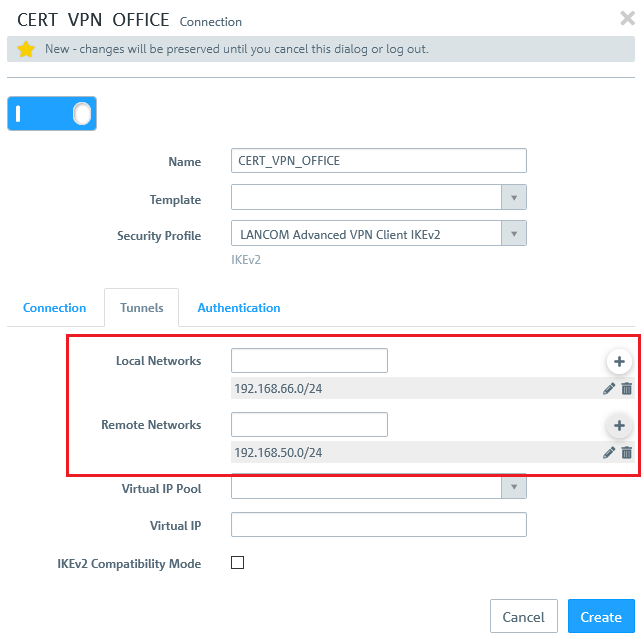
2,5) Open the Tunnels tab:
- Local networks: Here you enter the local networks (in CIDR notation) that the remote site should reach. In this example, the local network at the headquarters has the IP address range 192.168.66.0/24.
- Remote Networks: Here you enter the local networks (in CIDR notation) that the remote site should reach. In this example, the local network at the branch office has the IP address range 192.168.50.0/23.
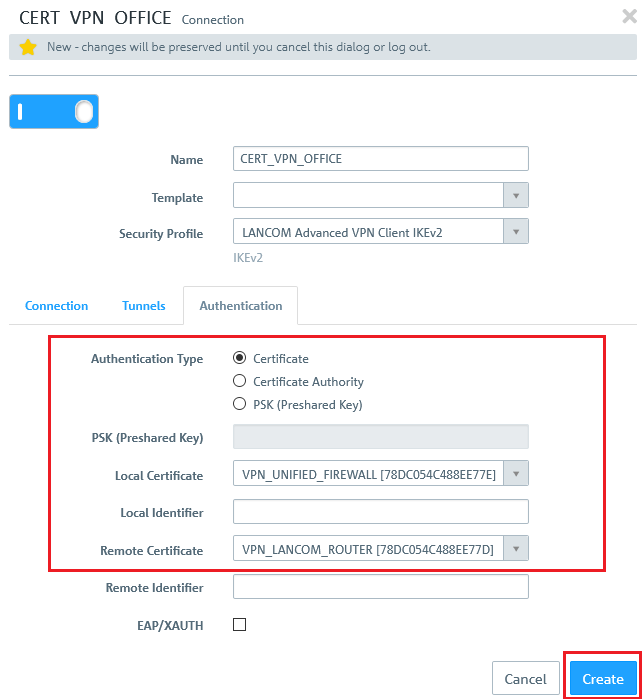
2.6) Change to the Authentication tab and enter the following parameters:
- Authentication type: Select the option Certificate here.
- Local certificate: Here you select the VPN certificate created for the Unified Firewall in step 1.6.
- Remote certificate: Here you select the VPN certificate created for the LANCOM router in step 1.4.
2.8) Click the icon to create a new VPN host.
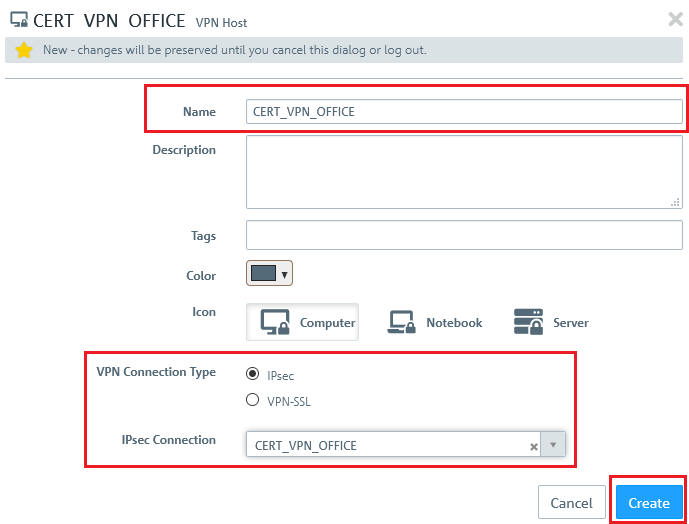
2.9) Save the following parameters:
- Name: Enter a descriptive name.
- VPN connection type: Select the type IPsec.
- IPsec connection: From the drop-down menu under IPsec, select the VPN connection created in steps 2.4 - 2.7.
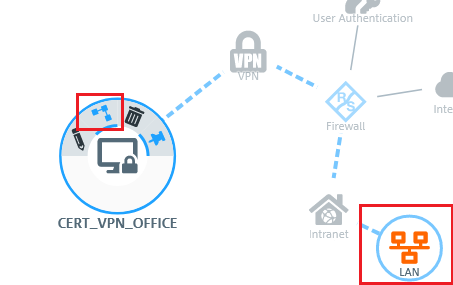
2.10) In the VPN host click on the "connection" icon and, to open the firewall objects, click on the network object that the object (the site-to-site connection) should access. Repeat this step for every network that the branch should be able to access.
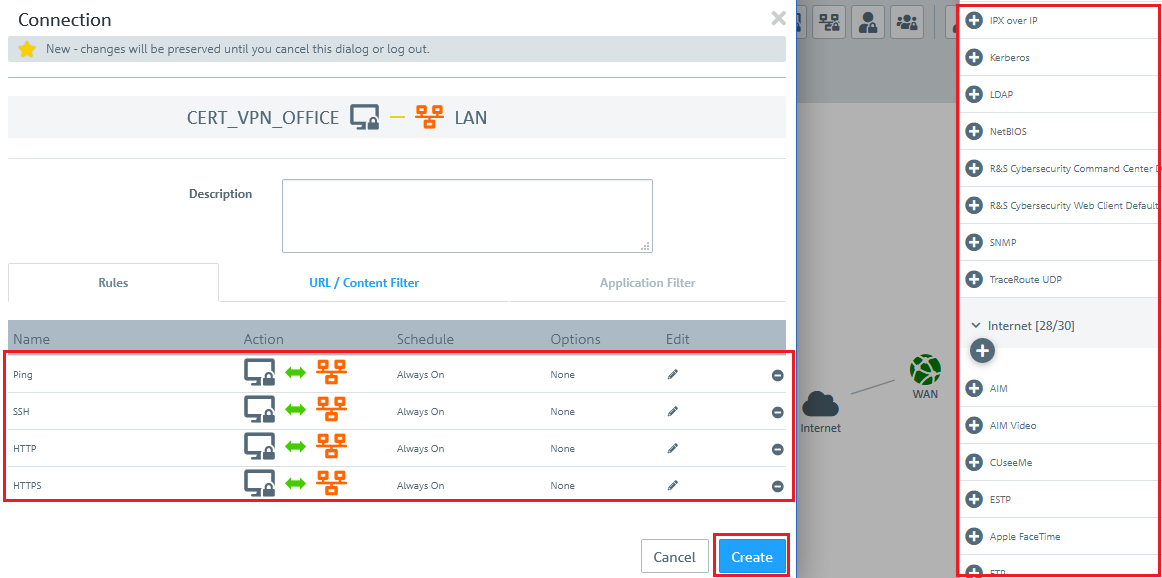
2.11) Use the "+" sign to assign the required protocols to the VPN host.
A Unified Firewall uses a deny-all strategy. You therefore have to explicitly allow communication.
2.12) Finally, implement the configuration changes by clicking Activate in the firewall.
2.13) This concludes the configuration steps on the Unified Firewall.
3) Export the VPN certificate for the LANCOM router at the branch office:
3.1) Change to the menu Certificate Management → Certificates and, for the VPN certificate for the LANCOM router, click the Export button.
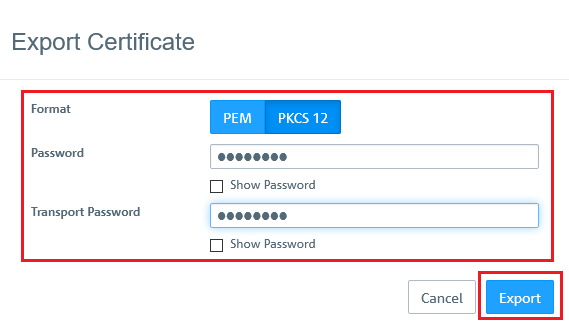
3.2) Select the PKCS 12 format and enter any password and a transport password.
3.3) Click Export and save the certificate file on your PC.
4) Configuration steps on the LANCOM router:
4.1) Upload the router certificate to the LANCOM router:
4.1.1) Right-click on the LANCOM router in LANconfig and select the option Configuration management → Upload certificate or file.
4.1.2) In the following dialog select the VPN certificate file exported in step 3.3) intended for the LANCOM router.
4.1.3) In the certificate type field, select a VPN container. This example uses the container "VPN1".
4.1.4) In the Cert. password box enter the password for the certificate file (see step 3.2).
4.1.5) Click on Open to start the upload.
4.2) Configure the certificate-based VPN connection on the LANCOM router:
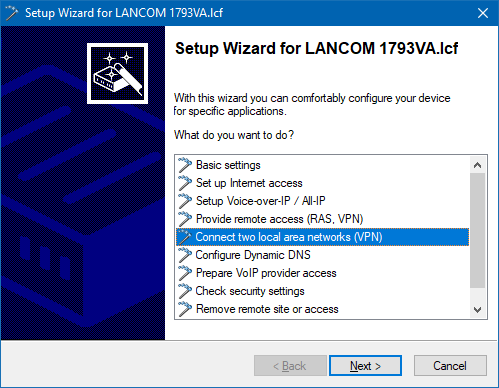
4.2.1) Start the Setup Wizard in LANconfig and select the option Connect two local area networks (VPN).
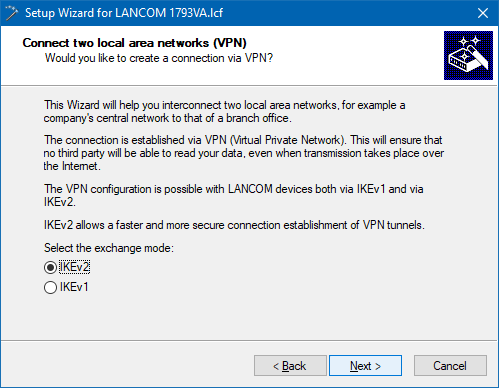
4.2.2) Select the option IKEv2.
4.2.3) In this example, we do not use IPsec-over-HTTPS.
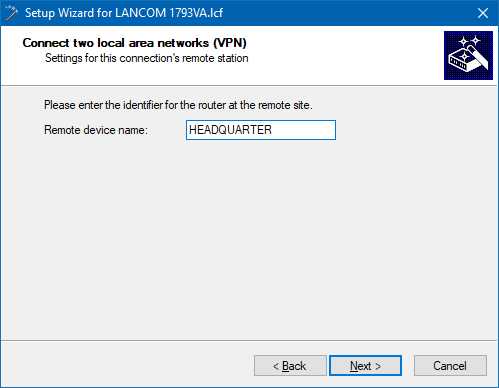
4.2.4) Enter a name for the new VPN connection.
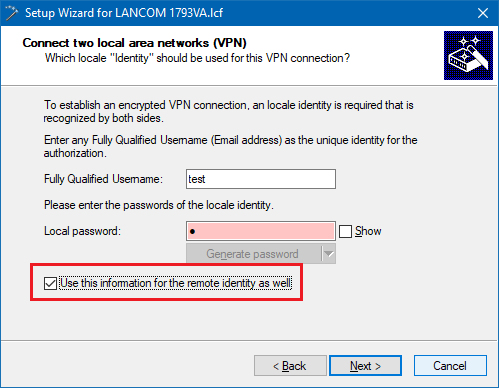
4.2.5) Enter any values into this dialog, as they will later be manually replaced in the configuration of the LANCOM router by the certificate authentication parameters (see step 4.2.11).
4.2.6) Activate the option Use this information for the remote identity as well.
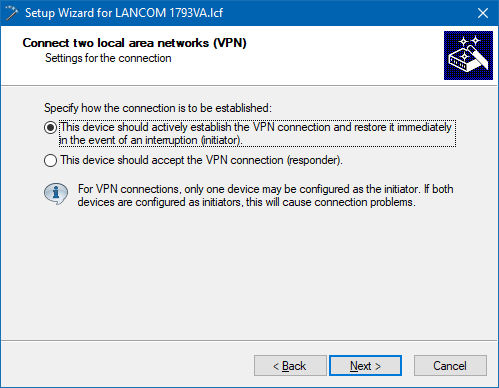
4.2.7) The LANCOM router at the branch office should establish the VPN connection.
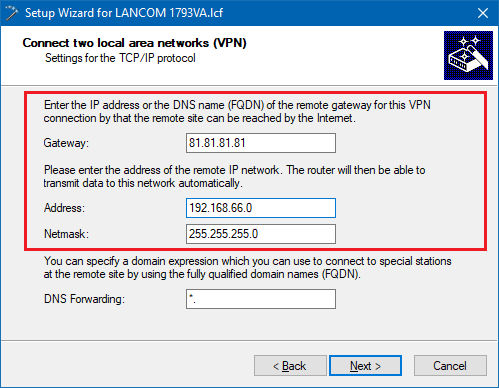
4.2.8) Enter the public IP address or the public DNS address of the LANCOM router at the headquarters and specify the relevant local IP address range at the remote site.
4.2.9) Click Finish to write the configuration back to the LANCOM router.
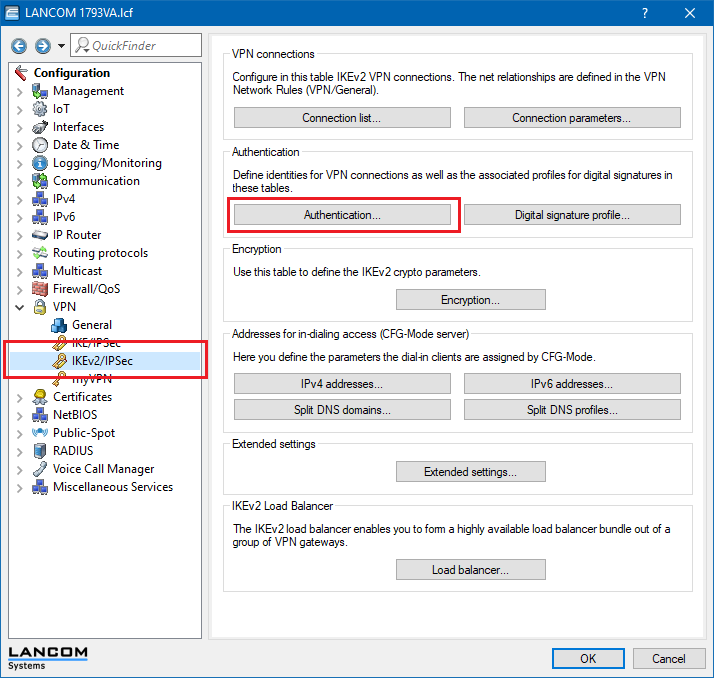
4.2.10) Open the configuration of the LANCOM router in LANconfig and navigate to VPN → IKEv2/IPsec → Authentication.
4.2.11) Select the available entry for the certificate-based VPN connection (in this case: HEADQUARTERS).
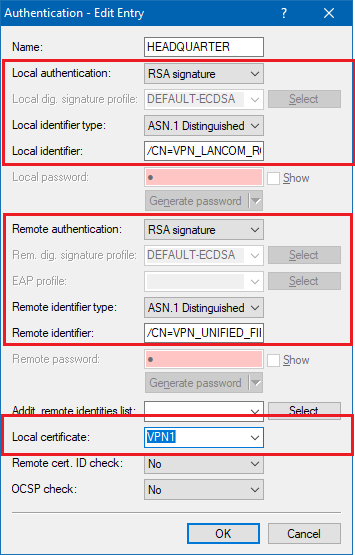
- Set the parameters for local and remote authentication for each entry to the values RSA signature and ASN.1 Distinguished Name.
- As the local identity, enter the name (CN, common name) of the certificate in the LANCOM router (see step 1.4).
- Enter the remote identity the name (CN, Common Name) of the certificate of the Unified Firewall (see step 1.6).
- As the Local certificate, select the VPN Container you used in step 4.1.3.
4.2.12) Write the configuration back to the LANCOM router.
The certificate-based VPN connection to the Unified Firewall at the headquarters will now be established.
5) Setting up port and protocol forwarding on a LANCOM router (scenario 2 only):
IPSec requires the use of the UDP ports 500 and 4500 as well as the protocol ESP. These must be forwarded to the Unified Firewall.
Forwarding the UDP ports 500 and 4500 automatically causes the ESP protocol to be forwarded.
If you are using a router from another manufacturer, ask them about appropriate procedure.
If the UDP ports 500 and 4500 and the ESP protocol are forwarded to the Unified Firewall, an IPSec connection to the LANCOM router can only be used if it is encapsulated in HTTPS (IPSec-over-HTTPS). Otherwise, no IPSec connection will be established.
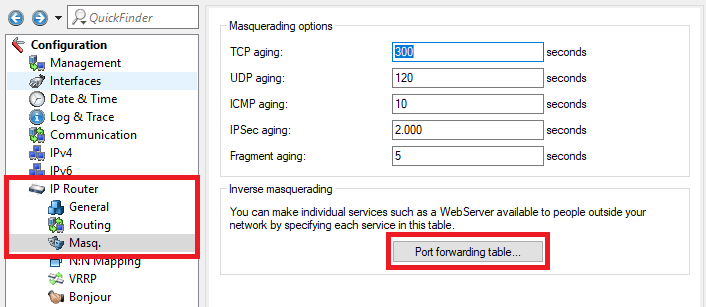
5.1) Open the configuration for the router in LANconfig and switch to the menu item IP-Router → Masq. → Port forwarding table.
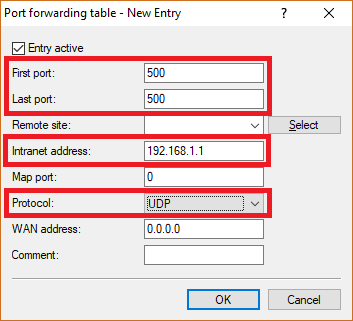
5.2) Save the following parameters:
- First port: Specify the Port 500.
- Last port: Specify the Port 500.
- Intranet address: Specify the IP address of the Unified Firewall in the transfer network between the Unified Firewall and the LANCOM router.
- Protocol: From the drop-down menu, select UDP.
5.3) Create a further entry and specify the UDP port 4500.
5.4) Write the configuration back to the router.