Description:
This article describes the different possibilities to secure access to a GS-23xx series switch from the local network.
Requirements:
- LCOS SX as of version 3.32 (download latest version)
- Any web browser for accessing the webinterface of the device
Procedure:
Possibility 1: Limiting management access to specific IP addresses or IP address ranges
If the switch is only accessed by devices with a specific IP address or from devices within a specific IP address range, it is practical to limit access accordingly. In doing so, the webinterface can only be invoked by a device with this IP address or from this IP address range.
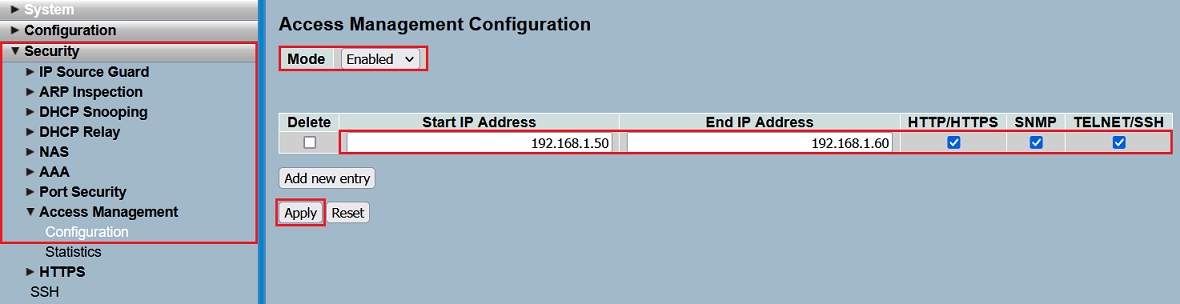
For this purpose, adjust the following parameters in the menu Security → Access Management → Configuration and click Apply:
- Set the Mode to Enabled.
- Specify an IP address range for Start IP Address and End IP Address from which access to the switch should be allowed. It is also possible to only allow access from a single IP address by entering the same IP address in both fields.
- Choose, which management protocols should be allowed for the IP address or IP address range (HTTP/HTTPS, SNMP, Telnet/SSH).
A maximum number of 16 entries can be created.
Possibility 2: Deactivate the protocol HTTP and activate the HTTPS redirect
LANCOM Systems recommends to deactivate the insecure protocol HTTP . Additionally it is practical to activate the automatic redirect to HTTPS, so that devices, which invoke the webinterface via HTTP, are redirected to the encrypted variant with HTTPS.
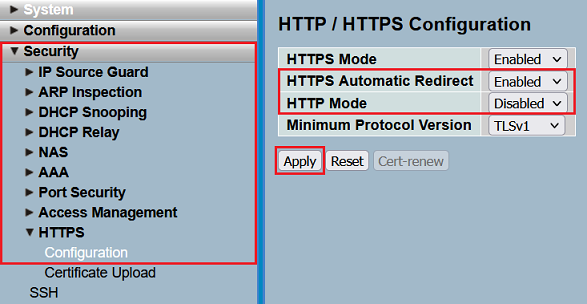
For this purpose, adjust the following parameters in the menu Security → HTTPS → Configuration and click Apply:
- HTTPS Automatic Redirect: In the dropdown menu select the option Enabled. In doing so a redirect to HTTPS takes place, when the webinterface is invoked via HTTP.
- HTTP Mode: In the dropdown menu select the option Disabled to deactivate the protocol HTTP.
Possibility 3: Deactivate login for insecure management protocols
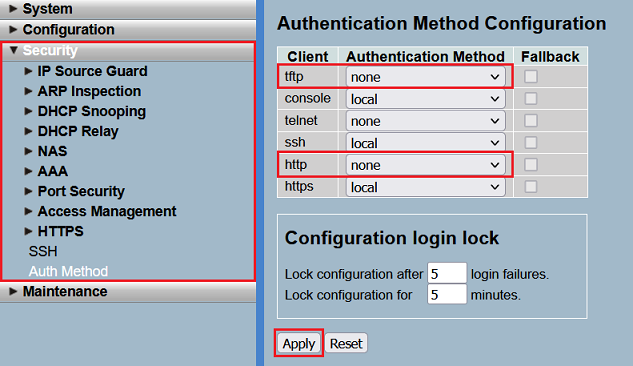
LANCOM Systems recommends to deactivate the login for the insecure protocols TFTP and HTTP. The login for the protocol Telnet is already deactivated in the factory defaults.
In the menu Security → Auth Method set the Authentication Method for the protocols TFTP and HTTP to none to deactivate the login. Click Apply afterwards.
This method does not deactivate the protocol itself, but only the login. For instance, when setting HTTP to none, the webinterface can still be invoked via HTTP, but the login is not possible.
Possibility 4: Configuration login lock
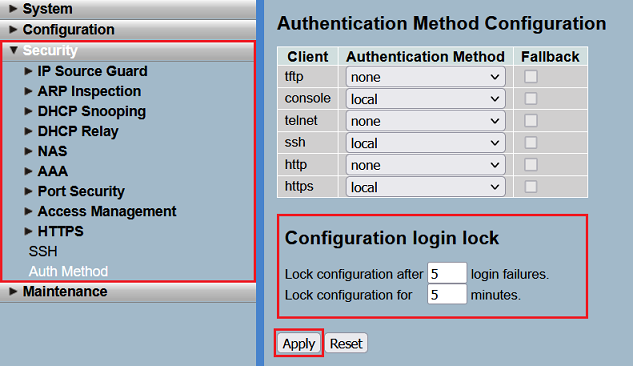
To make it more difficult to guess the login credentials through multiple login-attempts, there is a brute force protection in the switch.
Modify the values for the Configuration login lock in the menu Security → Auth Method, if necessary. Click Apply afterwards.
With factory defaults, after 5 login failures, the login is locked for 5 minutes for the used protocol.
Concluding step: Saving the start configuration
In order for configuration changes to be saved boot persistent, the configuration has to be saved as the start configuration.
Navigate to the menu Maintenance → Save/Restore → Save Start and click on Save so that the configuration is saved as a Start configuration.
The start configuration is retained even if the device is restarted or there is a power failure.