Description:
This document describes how you can create digital certificates with LANCOM Smart Certificate for authenticating certificate-based VPN connections (site-to-site or client-to-site).
Requirements:
- LCOS as of version 9.10 (download latest version)
- LANtools as of version 9.10 (download latest version)
- LANCOM central-site gateway, WLAN controller, or LANCOM router with an activated VPN 25 Option
The LANCOM router must have up-to-date time settings. Information on configuring time synchronization can be found in this article.
Procedure:
Configuring certificates for VPN connections:
By using LANCOM Smart Certificate, the digital certificates required for certificate-based VPN connections can be created directly on the LANCOM router.
The procedure is the same for all VPN scenarios. Each communication partner (router or VPN client) requires its own certificate.
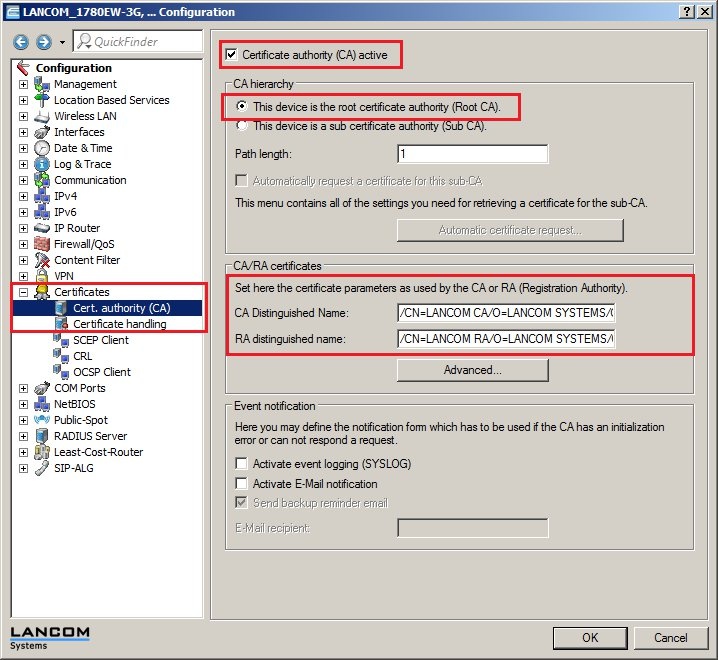
1.1) In LANconfig, open the configuration dialog for the LANCOM router and switch to the menu item Certificates → Cert. authority (CA).
1.2) Set a check mark for the option Certificate authority (CA) active. The LANCOM router functions as the root certificate authority (root CA).
For this configuration example we leave all of the other parameters with their preset values.
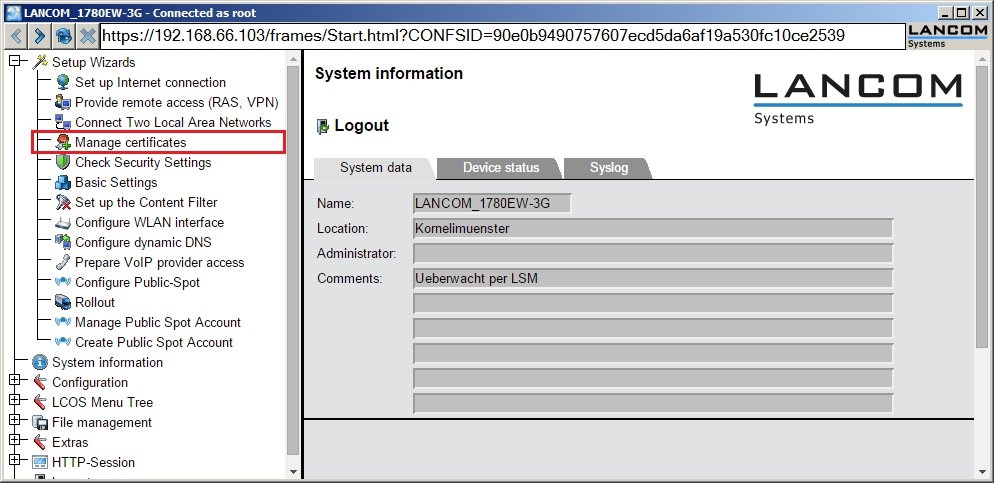
1.3) In WEBconfig, access the configuration for the LANCOM router and switch to the menu item Setup Wizards → Manage certificates.
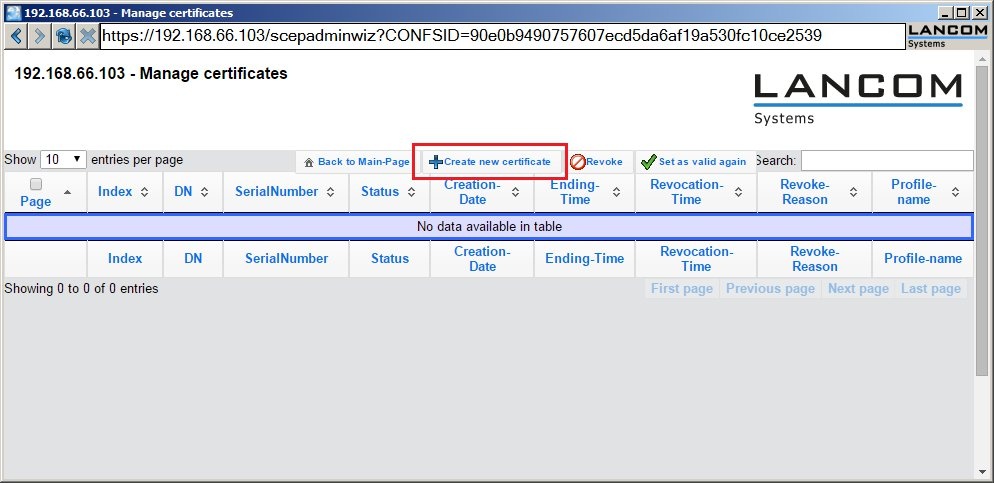
1.4) First, create the certificate for the LANCOM router. Click the button Create new certificate to do this.
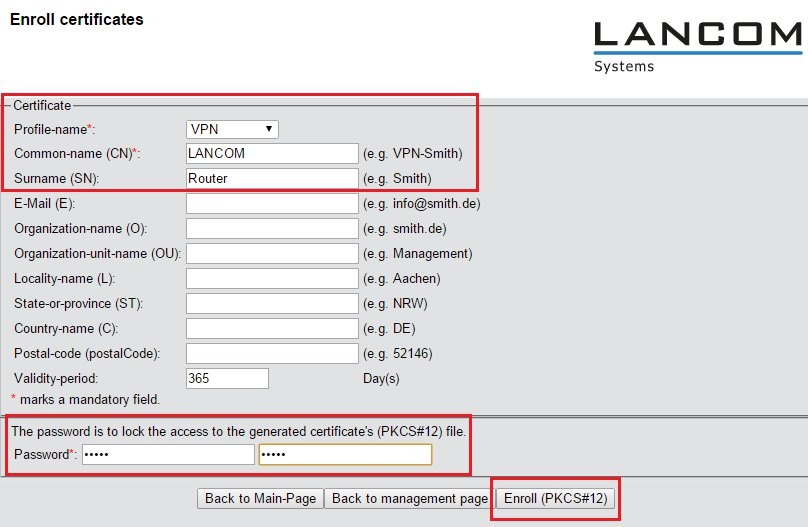
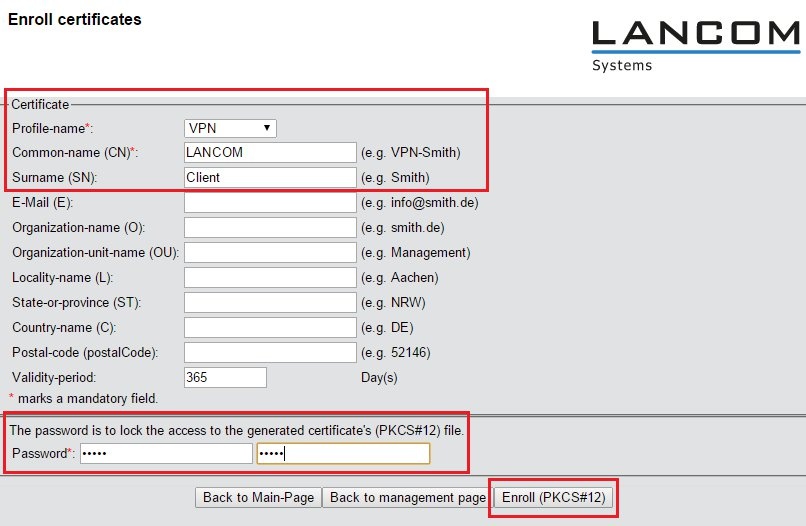
1.5) Set the profile name to VPN.
1.6) In this example, the common name (CN) is set as the company's name. By way of example, the surname (SN) is set to the descriptor Router. The other fields can be filled in as you desire.
1.7) Be sure to password-protect the certificate container.
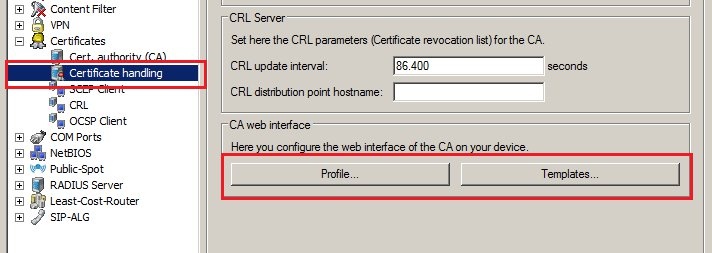
You can specify which profiles and fields should be displayed in this form in the LANCOM router's configuration with the menu items Certificates → Certificate handling → Profiles and Templates.
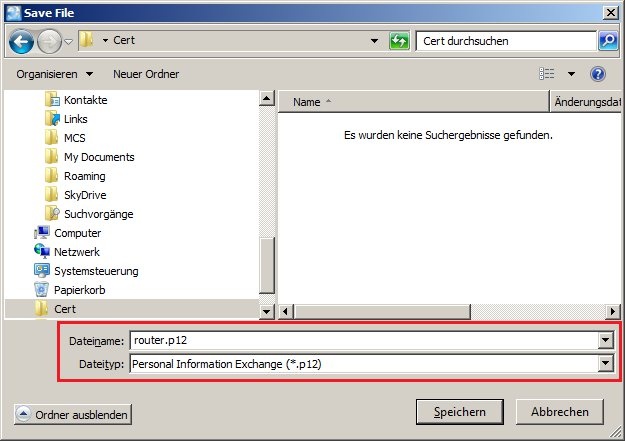
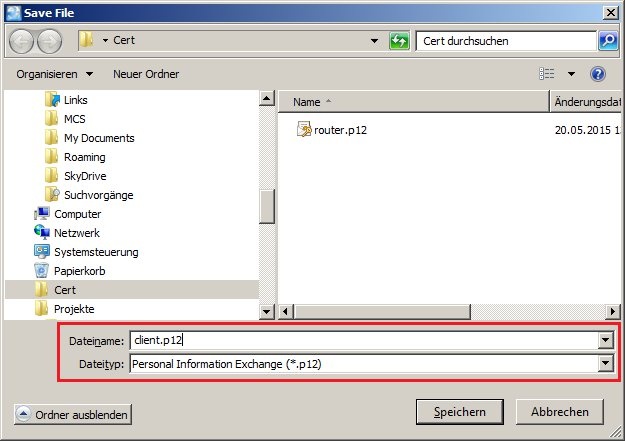
1.8) Click the button Enroll (PKCS#12) and give the certificate file a unique file name, if necessary.
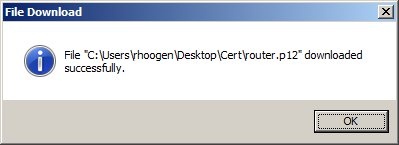
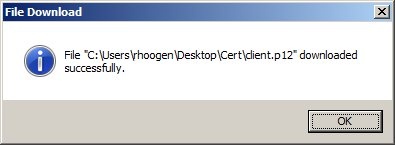
1.9) The successful download of the certificate file is confirmed by a message.
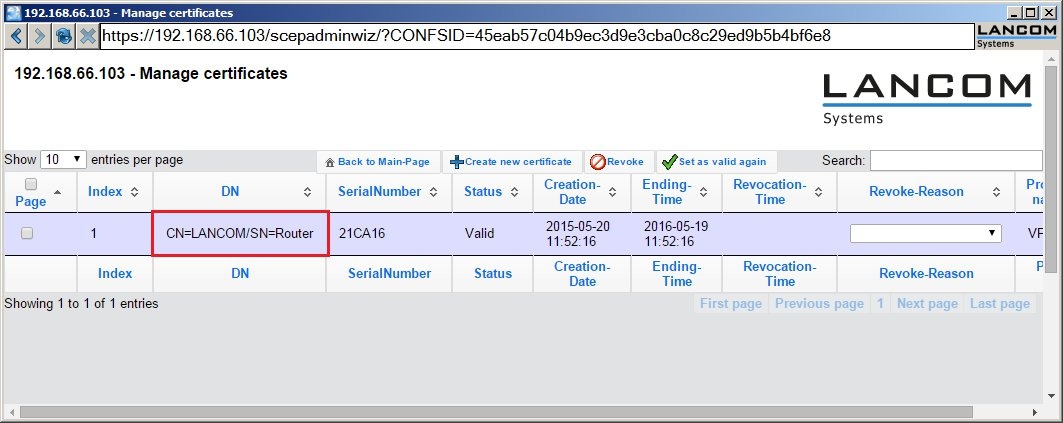
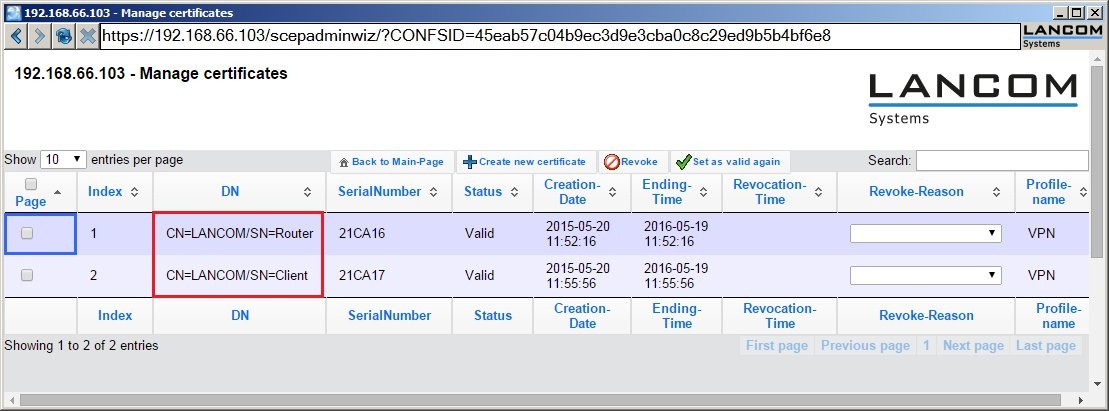
1.10) If you switch back to Manage certificates, you should see the created certificate in the list.
1.11) Create an additional certificate for the VPN Client by clicking on the button Create new certificate once again.
1.12) Set the profile name to VPN.
1.13) In this example, the common name (CN) is set as the company's name. By way of example, the surname (SN) is set to the description Client. The other fields can be filled in as you desire.
1.14) You need to password-protect the certificate container.
1.15) Click the button Enroll (PKCS#12) and give the certificate file a unique file name, if necessary.
1.16) The successful download of the certificate file is confirmed by a message.
1.17) If you switch back to the Manage certificates, you should see the created certificate in the list.
1.18) The certificates should have been created successfully and can now be used for the authentication of certificate-based VPN connections.
- Configuring a certificate-based IKEv2 VPN client connection in the LANCOM Advanced VPN Client
- LANCOM Smart Certificate: Creating and using certificates for a VPN connection with certificate distribution by SCEP
- Configuring a certificate-based VPN connection between two LANCOM routers (IKEv2) with digital signature authentication