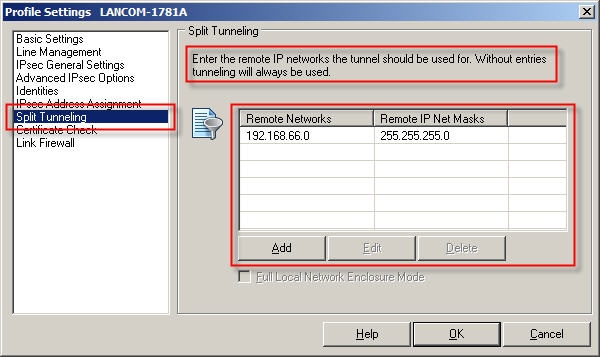
 Image Added
Image Added
Step 4:
Check if you require an IPSec pass-through, or whether this has been set up already.
By default an IPSec connection uses the port 500 UDP, the IP protocol ESP (50), or port 4500 UDP. The VPN tunnel may occasionally be directed via routers which do not support IPSec pass-through. In these cases, the IPSec packets may be handled incorrectly, or they may even be dropped.
A result of this is that, even though the tunnel has been established, it cannot be used for communications. This problem can be avoided by activating port forwarding for the UDP ports 500 and 4500 on the client-side of the router.
Step 5:
If you cannot use IPSec pass-through, you have the option of setting up a VPN connection based on IPSec over HTTPS. All you have to do in this case is to open the HTTPS port 443.
With IPSec over HTTPS, an attempt is first made to transfer data using standard IPSec. If the connection cannot be established (e.g. because IKE port 500 is blocked), then an attempt is then automatically made to establish a connection that encapsulates the IPSec VPN in an additional SSL header (port 443, like HTTPS).
For a guide on setting up a VPN with IPSec over HTTPS, see this KnowledgeBase document (





























