...
| Hinweis |
|---|
|
Requirements:
- LCOS as of version 9.0 (download latest Version)
- LANtools as of version 9.0 (download latest Version)
- The second WLAN Controller (Slave) must must be unconfigured and still with its factory settings!
- The option Certificate authority (CA) active in the menu Certificates → Cert. authority (CA) on the second WLAN Controller (Slave) must not be active!
...
1.1) Perform the basic setup of the WLAN controller as described in this knowledge base article.
1.2) Then configure the WLAN profiles as required. Here are two examples:
- WLAN layer-3 tunneling tutorial: WLAN controller with Public Spot
- Manually configuring a guest network on a WLAN controller by means of VLAN
1.3) Change to the menu Management → General and set a descriptive Device name.
...
2) Configuring the second WLAN controller (slave):
...
| Hinweis |
|---|
The second WLAN controller must be unconfigured and still with its factory settings! |
2.1) Save the configuration of the first WLAN controller as a script file.
2.2) Open the script backup in a text editor and edit the following items:
...
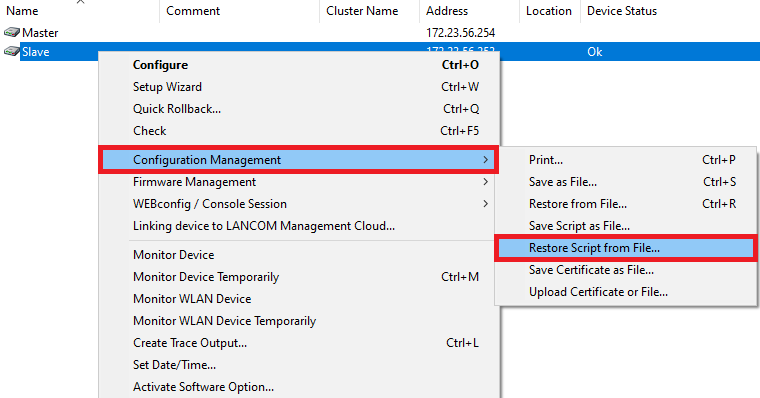
2.3) Upload your customized script backup to the second WLAN controller: Right-click on the slave WLAN controller and, in the context menu, click Configuration management → Restore script from file.
...
| Info |
|---|
Alternatively you can |
...
use LANconfig and drag & drop the script file from your folder onto the WLAN controller. |
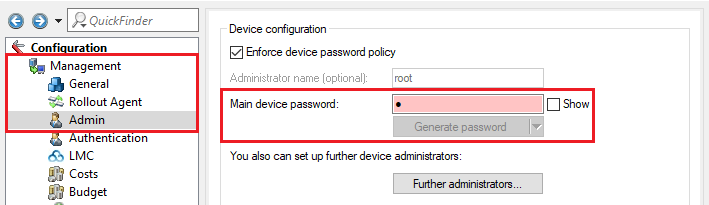
2.4) Change to the menu Management → Admin and set a Main device password.
...
| Info |
|---|
The Main device password is not included in a script backup, so it has to be set manually afterwards. |
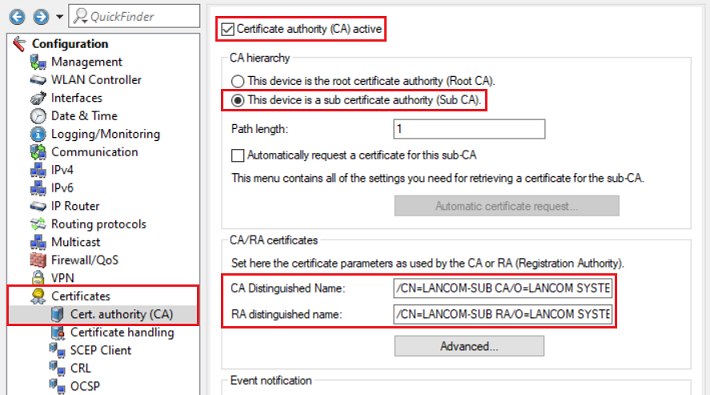
2.5) Change to the menu Certificates → Cert. authority (CA) and modify the following parameters:
- Set a checkmark next to Certificate authority (CA) active.
- Select the radio button This device is a sub certificate authority (Sub-CA).
- Set a checkmark next to Automatically request a certificate for this sub-CA.
- Adjust the Common Name (CN) of the CA Distinguished Name (i.e. /CN=LANCOM-SUB).
- Adjust the Common Name (CN) of the RA Distinguished Name (i.e. /CN=LANCOM-SUB).
2.6) Go to the menu Automatic certificate request.
2.7) Enter the following parameters:
...
)
...
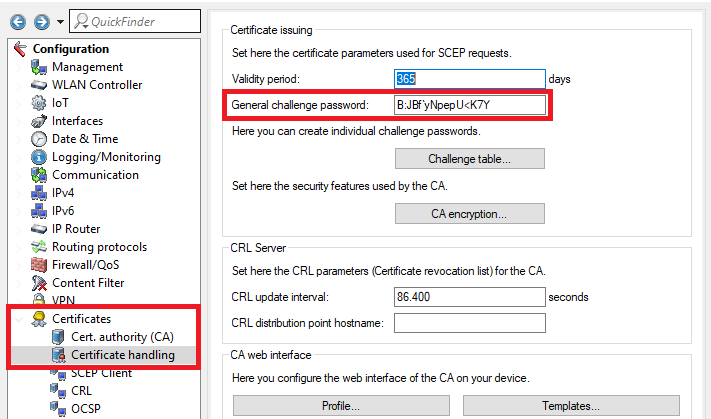
2.8) Change to the menu Certificates → Certificate handling and enter the General challenge password of the master WLAN controller (see step 1.5).
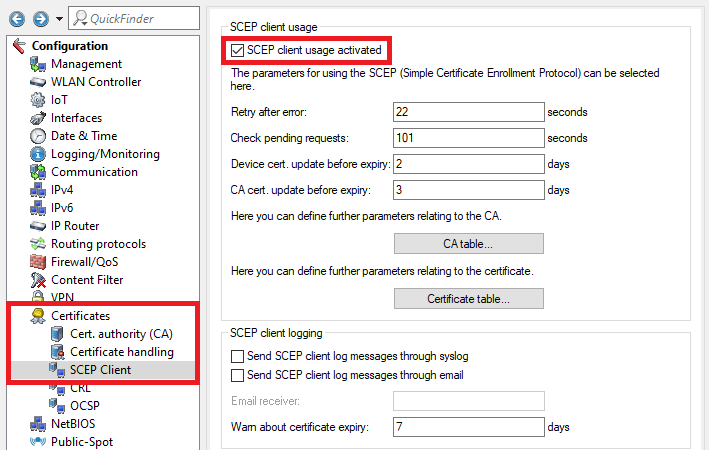
2.97) Go to the menu Certificates → SCEP client and set a checkmark next to SCEP client usage activated.
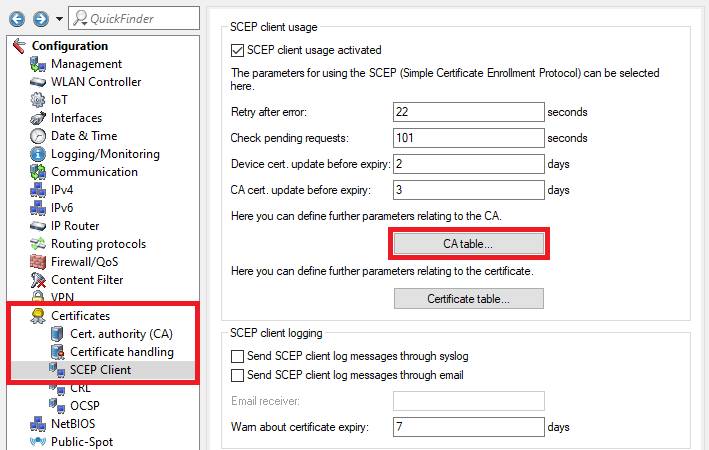
2.108) Go to the menu CA table.
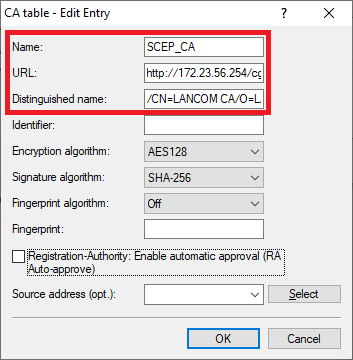
2.119) Two entries have to be created in the CA table. One entry serves to obtain a controller certificate from the device’s own certificate authority and the second entry serves to obtain the CA from the master WLAN controller.
...
- Name: Enter a descriptive name (in this example SCEP_CA).
- URL: Enter the URL http://172.23.56.254/cgi-bin/pkiclient.exe . If necessary, change the IP address 172.23.56.254 to the IP address of the master WLAN controller.
- Distinguished name: Enter the CA distinguished name of the master WLAN controller (see step 1.4).
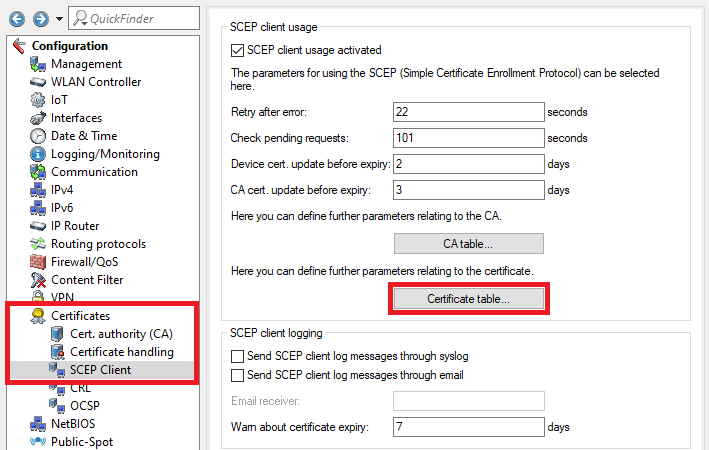
2.1210) Go to the menu Certificate table.
2.1311) Three entries have to be created in the certificate table. These specify more detailed information for individual certificates, such as the Key length and Subject. This is necessary so that certificates with the required characteristics can be created and obtained.
...
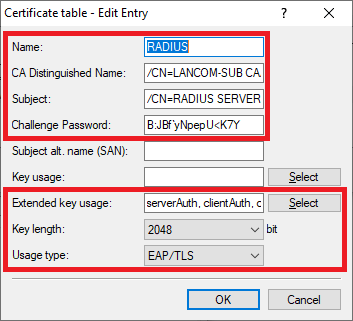
- Name: Enter a descriptive name (in this example RADIUS).
- CA distinguished name: Enter the CA distinguished name of the slave WLAN controller (see step 2.5).
- Subject: Set the Subject to /CN=RADIUS SERVER/O=LANCOM SYSTEMS/C=DE.
- Challenge password: Enter the challenge password of the master WLAN controller (see step 1.5).
- Extended key usage: In the selection menu, set check marks for the options serverAuth, clientAuth and critical.
- Key length: From the drop-down menu, select 2048.
- Usage type: From the drop-down menu, select EAP/TLS.
2.1412) This concludes the configuration of the slave WLAN controller. You can now write the configuration back to the device.
...