Make sure that the DNS server of your LANCOM R&S®Unified Firewall correctly resolves the domains it accesses when the HTTP(S) proxy is active. The DNS server of the Unified Firewall has to be entered on the network devices (static or dynamic via DHCP). As an alternative a separate local DNS server can be used. This DNS server has to forward the DNS requests to the DNS server of the Unified Firewall. Furthermore a DNS cache must not be used on the end devices or a local DNS server. In order for the connection to be established the IP addresses resolved by the end device and the Unified Firewall must match. If there is a discrepancy the error message "Host header forgery detected" is displayed in the Unified Firewall log. Access to the requested website is not possible in this case! This can also lead to performance issues when accessing a website! When the Google DNS servers are used (8.8.8.8 and 8.8.4.4), "Host header forgery" messages can occur even if the DNS configuration in your scenario is correct. In this case please use another DNS server. | 

 )
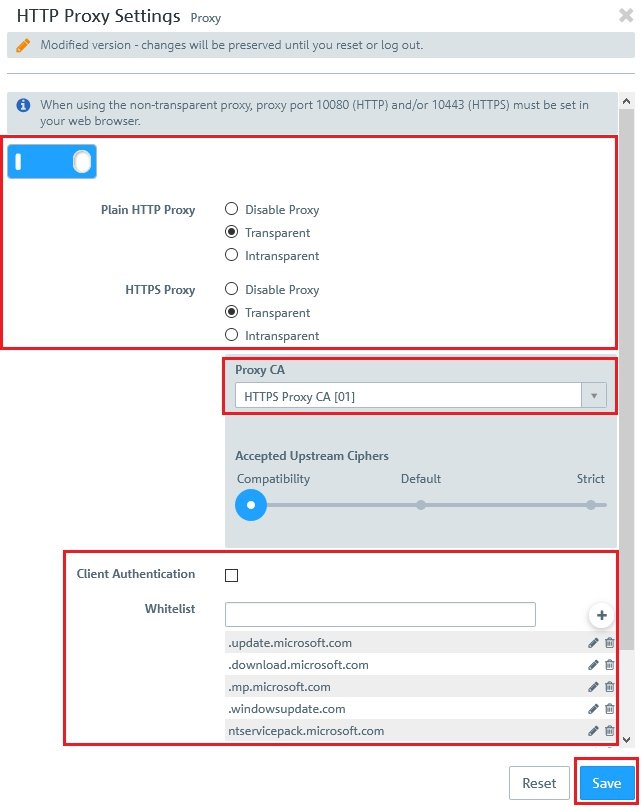
)

 )
)

