Desvription:
This document contains information on the measures that can be taken against the "LocalNet" and "ServerIP" attacks described by Mathy Vanheof in the paper "Leaking VPN Client Traffic by Abusing Routing Tables" (#VU563667).
With the attacks described, it is important to mention that they do not compromise the actual VPN tunnel. Data transmitted through the VPN tunnel is still secure.
Rather, attempts are made to redirect data traffic intended for the VPN tunnel to another destination before the tunnel in order to then be able to read it in plain text.
In the application scenarios usually used by our customers (secure VPN client access, e.g. from the home network to the company network), this can only succeed if an attacker has access not only to the local network in which the VPN client is currently located, but also to the (company) network to which the VPN tunnel connects.
Therefore, for example, VPN client connections that a company uses to provide its employees with secure access to the company network are less likely to be affected by attacks.
In public (WLAN) networks and/or when using public VPN servers, however, these attack possibilities pose a certain danger, which is why the countermeasures described in this document should be implemented there in any case.
All attacks and their variants are described in the following CVE messages in addition to the explanations in the paper:
LocalNet attacks:
ServerIP attacks:
In the default setting, both the Advanced VPN Clients for Windows and macOS are vulnerable to both attacks (LocalNet and ServerIP).
We have compiled detailed technical information on this topic for you in a PDF document:
1. LANCOM Advanced VPN Client for Windows
1.1 Countermeasurements against LocalNet attacks
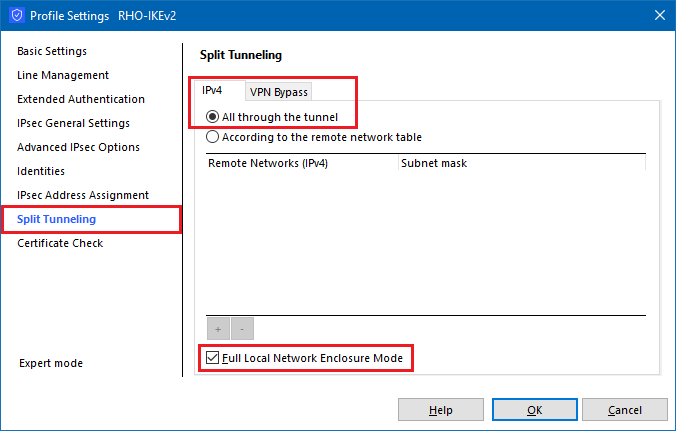
For the LANCOM Advanced VPN Client for Windows, the LocalNet attack can be prevented by enabling the “Full Local Network Enclosure Mode” option. As a result, all network traffic will be sent through the tunnel.
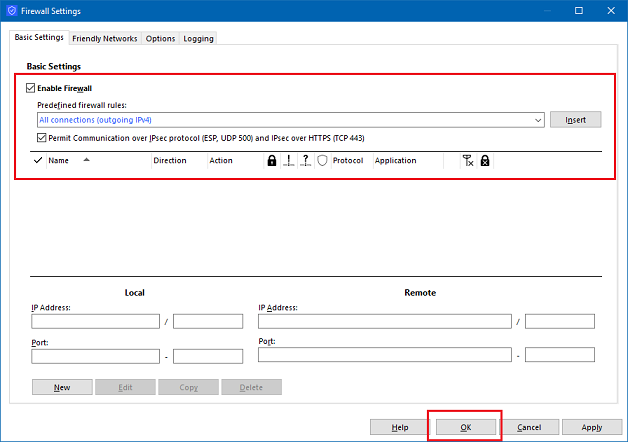
Alternatively, the integrated Advanced VPN Client Firewall can be configured such that only VPN traffic is allowed outside the tunnel (using the “Permit IPsec protocol” firewall option), with dedicated exceptions for, e.g., the local network printer.
1.2 Countermeasurements against ServerIP attacks
The traffic leak to arbitrary IP addresses (CVE-2023-36673) can be prevented by configuring an IP address instead of a domain name in the VPN configuration. Authenticated DNS variants (DNSSEC) are not supported yet.
Additionally, the integrated Advanced VPN Client Firewall can be configured such that only VPN traffic is allowed outside the VPN tunnel. This can be achieved by setting the “Permit IPsec protocol” firewall option and removing all other firewall rules (see step 1.1).
2. LANCOM Advanced VPN Client for macOS
2.1 Countermeasurements against LocalNet attacks
For the LANCOM Advanced VPN Client for macOS, the LocalNet attack can be prevented only partially by enabling the “Full Local Network Enclosure Mode” option. Network traffic to and from the standard gateway will not be routed into the VPN tunnel.
Alternatively, a third-party firewall can be configured such that only VPN traffic is allowed outside the tunnel, with dedicated exceptions for, e.g., the local network printer.
2.1 Countermeasurements against ServerIP attacks
The traffic leak to arbitrary IP addresses (CVE-2023-36673) can be prevented by configuring an IP address instead of a domain name in the VPN configuration. Authenticated DNS variants (DNSSEC) are not supported yet.
Additionally, a third-party firewall can be configured such that only the VPN protocols are allowed outside the VPN tunnel, which are ISAKMP (UDP port 500) and IPsec NAT-T (UDP port 4500).