Description:
If a server in the local network (e.g. a web server) should be reachable via the internet, a port forwarding can be used. Albeit a port forwarding has the downside that the same port can only be used once. If several domains are hosted on one web server, a Reverse Proxy has to be used. It recognizes the invoked domain and relays it to the corresponding web server. Furthermore, with a Reverse Proxy a Loadbalancing as well as a backup can be implented, when several servers are entered in the Backend.
This article describes how a Reverse Proxy can be configured on a Unified Firewall.
Requirements:
- LANCOM R&S® Unified Firewall mit Firmware ab Version 10.2
- Bereits eingerichtete und funktionsfähige Internet-Verbindung auf der Unified Firewall
- Bereits eingerichteter und funktionsfähiger Web-Server
- Vorhandenes SSL-Zertifikat einer öffentlichen Zertifizierungsstelle (CA) im PKCS12 Format
- Web-Browser zur Konfiguration der Unified Firewall.
Es werden folgende Browser unterstützt:- Google Chrome
- Chromium
- Mozilla Firefox
Scenario:
1. Die Unified Firewall ist direkt mit dem Internet verbunden
- Die Unified Firewall baut die Internet-Verbindung auf. Diese hat die öffentliche IP-Adresse 81.81.81.1, die mit dem DNS-Namen web-server.lancom.de verknüpft ist.
- Ein Web-Server im lokalen Netzwerk der Unified Firewall mit der IP-Adresse 192.168.1.200 soll aus dem Internet per HTTPS erreichbar sein.
2. Ein Router vor der Unified Firewall baut die Internet-Verbindung auf
- Ein vorgeschalteter Router vor der Unified Firewall baut die Internet-Verbindung auf. Dieser hat die öffentliche IP-Adresse 81.81.81.1, die mit dem DNS-Namen web-server.lancom.de verknüpft ist.
- Die Unified Firewall und der vorgeschaltete Router sind beide Mitglied im Transfer-Netzwerk 192.168.0.0/24. Die Unified Firewall hat dort die IP-Adresse 192.168.0.254.
- Ein Web-Server im lokalen Netzwerk der Unified Firewall mit der IP-Adresse 192.168.1.200 soll aus dem Internet per HTTPS erreichbar sein.
Procedure:
Die Einrichtung bei Szenario 1 und 2 ist grundsätzlich gleich. Bei Szenario 2 muss zusätzlich noch ein Portforwarding auf dem vorgeschalteten Router eingerichtet werden.
1) Configuring the Reverse Proxy on a Unified Firewall (scenario 1 and 2)
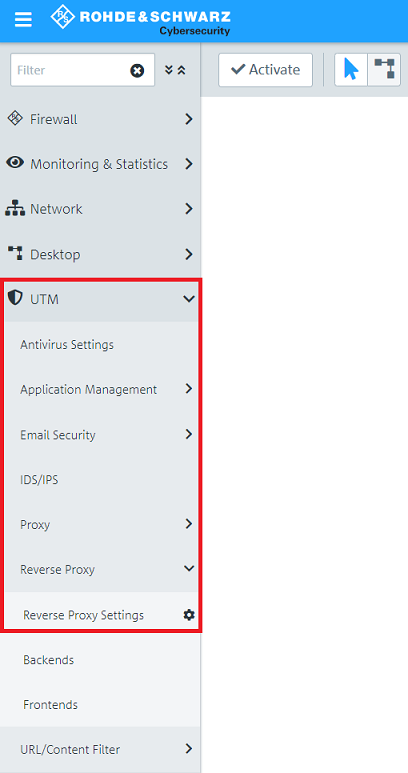
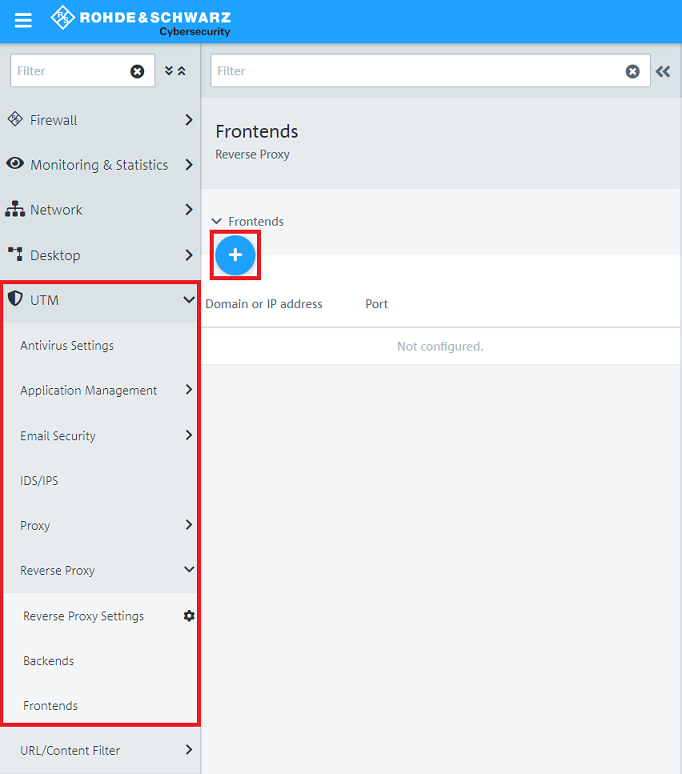
1.1) Open the configuration of the Unified Firewall in a browser and go to the menu UTM → Reverse Proxy → Reverse Proxy Settings.
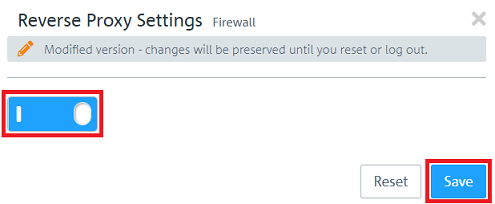
1.2) Activate the Reverse Proxy via the slider and click Save.
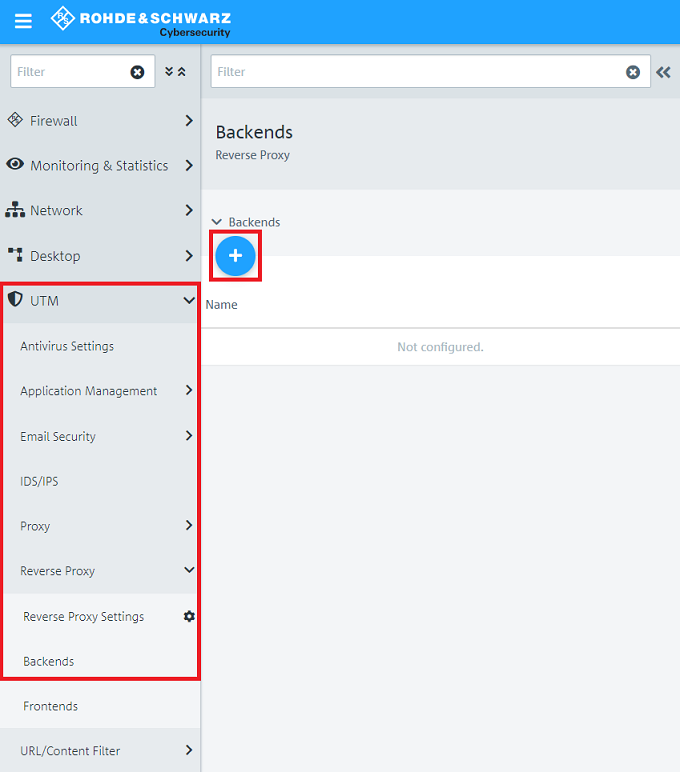
1.3) Go to the menu Backends and click on the "Plus symbol" to create a new Backend.
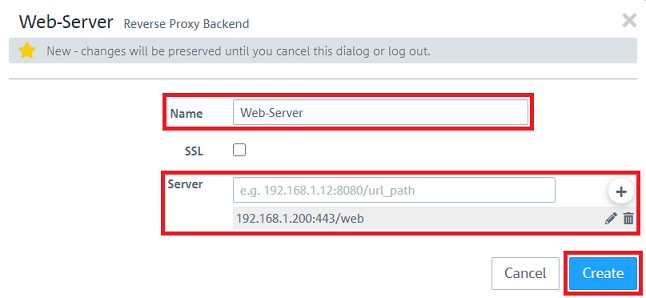
1.4) Change the following parameters and click Create:
- Name: Assign a meaningful name for the Backend.
- Server: Enter the IP address of the server in the local network as well as the port and the URL path and add the entry by clicking on the "Plus symbol".
Optionally you can activate SSL encryption to encrypt the connection between the Unified Firewall and the server in the local network.
1.5) Go to the menu Frontends and click on the "Plus symbol" to create a new Frontend.
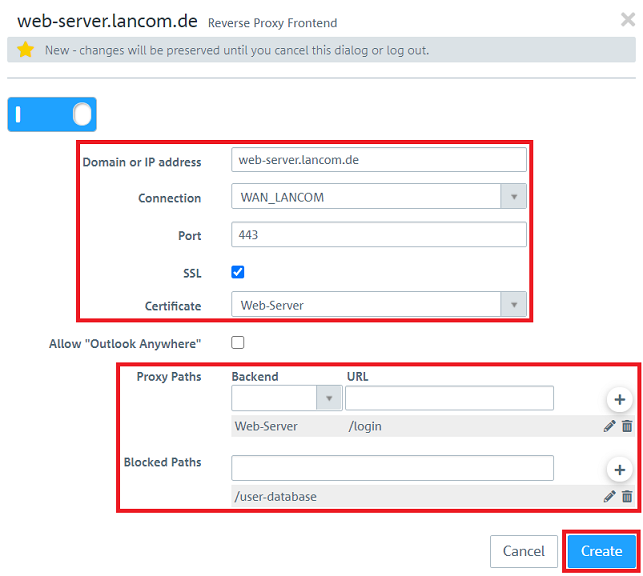
1.6) Make sure, that the slider is active, change the following parameters and click Create:
- Domain or IP address: Enter the public IP address or the DNS name where the server should be reachable.
- Connection: In the dropdown-menu select the Internet connection of the Unified Firewall.
- Port: Enter the Port to be used for contacting the server from the Internet.
- SSL: It is recommended to encrypt access from the Internet to the server. Therefore activate the option.
- Certificate: In the dropdown-menu select the SSL certificate to be used for authentication. It has to be imported in the menu Certificate Management → Certificates.
The SSL certificate has to be obtained from a public certification authority (CA) in order for any party to gain access to the server. The root certificate of known public certificate authorities is usually included in the certificate store of end devices.
Thus the certificate cannot be created on a Unified Firewall. In this case the certificate would have to be exported on the Unified Firewall and imported to the end device of each party, which should have access to the server.
- Proxy Paths: In the dropdown-menu select the Backend created in step 4) and enter the URL access should be allowed to. Add the entry by clicking on the "Plus symbol".
- Blocked Paths: Optionally, enter one or more URLs the access should not be allowed to. Add the entry by clicking on the "Plus symbol".
1.7) The configuration of the Reverse Proxy on the Unified Firewall is thereby complete.
2) Setting up port forwarding on an upstream LANCOM router (scenario 2 only)
If you are using a router from another manufacturer, approach them for information about the appropriate procedure.
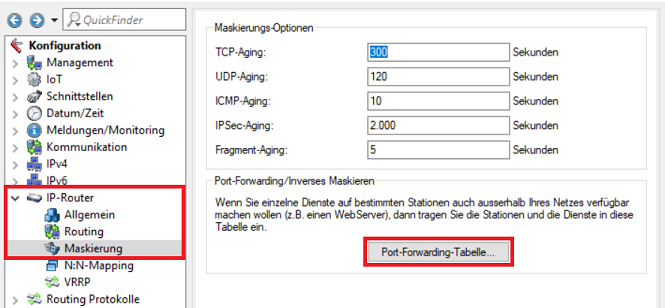
2.1) Open the configuration for the LANCOM router in LANconfig and switch to the menu item IP Router → Masqu. → Port forwarding table.
2.2) Create a new entry and adjust the following parameters:
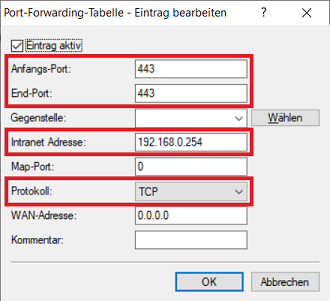
- First port: Enter the port to be forwarded (in this example port 443 for HTTPS).
- Last port: Enter the port to be forwarded (in this example port 443 for HTTPS).
- Intranet address: Enter the IP address of the Unified Firewall in the intermediate network between the Unified Firewall and the LANCOM router (the Unified Firewall has the IP address 192.168.0.254 in this example).
- Protocol: Select the associated protocol from the drop-down menu (HTTPS uses TCP).
2.3) This concludes the configuration of the router. Write the configuration back to the router.