Description:
There is no need for the IKE and IPsec lifetimes to be the same at both ends. Rekeying is initiated shortly before the negotiated lifetime expires, usually after the shorter of the two routers’ lifetimes. However, under certain circumstances the connection may be lost during rekeying. If this is the case, it may be worthwhile to increase the lifetimes so that disconnections occur less often. This does require the lifetimes on both routers to have the same or at least a very similar values.
For security reasons, the lifetimes should not be too long, otherwise the keys could be compromised. Equally, the lifetimes should not be too short in order to avoid frequent and time-consuming rekeying.
This article describes how to adjust the IKEv1 lifetimes on a LANCOM router.
Regarding the configuration of lifetimes on a third-party device, please contact the manufacturer.
Requirements:
- LCOS as of version 8.50 (download latest version)
- LANtools from version 8.50 (download latest version)
- A configured and functional IKEv1 VPN connection
- Information about the lifetimes must be available or freely selectable at both ends
- SSH client such as PuTTY for access to the command line
Procedure:
1) Adjust the IKE lifetimes (phase 1):
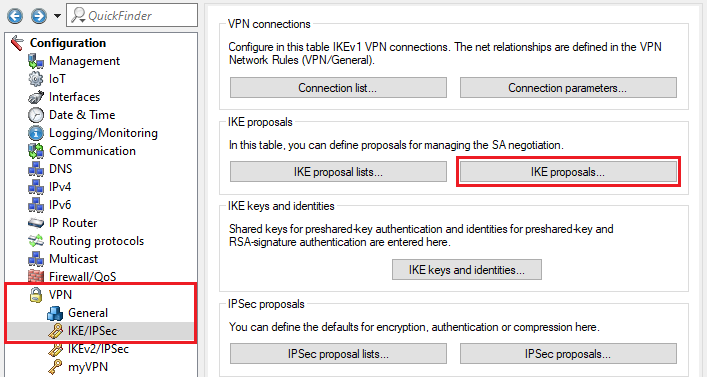
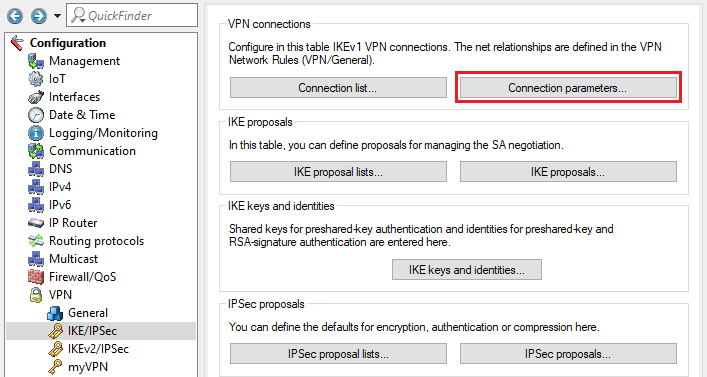
1.1) Open the configuration of the router in LANconfig and navigate to VPN → IKE/IPSec → IKE proposals.
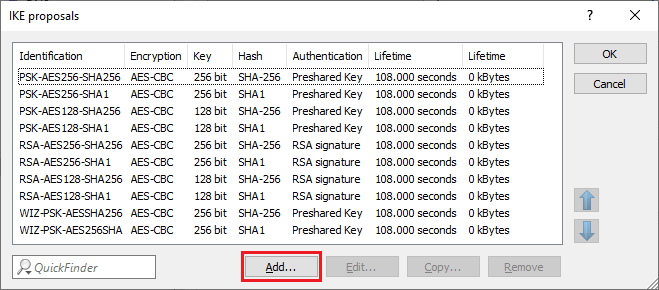
1.2) Click on Add to create a new proposal.
Under no circumstances should you edit or adapt the existing default proposals, otherwise other VPN connections that use the adapted proposal may no longer function correctly.
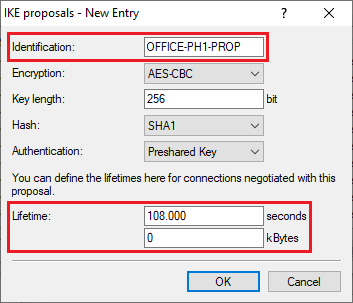
1.3) Enter the encryption settings as for the previous VPN connection and adjust the following parameters:
- Identification: Enter a descriptive name (in this example OFFICE-PH1-PROP). The key length is limited to 17 characters.
- Lifetime: Enter the required lifetime in seconds. A lifetime in kBytes is not configured in phase 1 because very little data is transferred here. In this case leave the value at the default setting 0 kBytes.
LANCOM Systems recommends a maximum lifetime of 108,000 seconds (corresponds to the default setting). As of November 2021, the BSI (German Federal Office for Information Security) recommends a maximum lifetime of 86,400 seconds (1 day) for IKEv2.
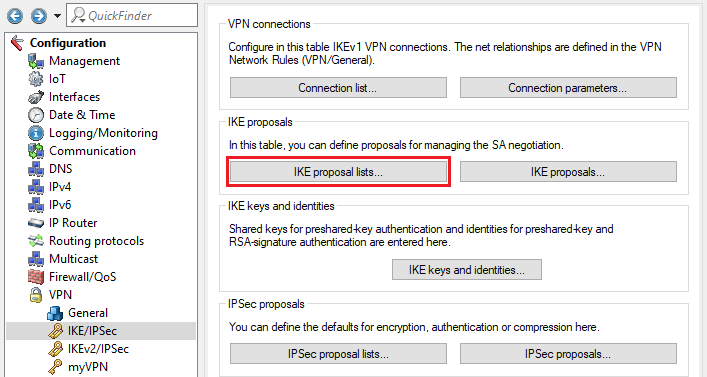
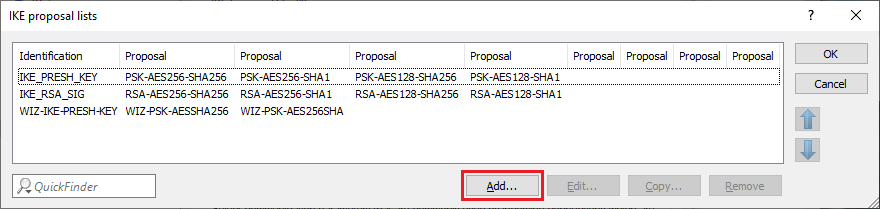
1.4) Navigate to the IKE proposal lists menu.
1.5) Click on Add to create a new IKE proposal list.
Under no circumstances should you edit or adapt the existing IKE proposal lists, otherwise other VPN connections that use the adapted list may no longer function correctly.
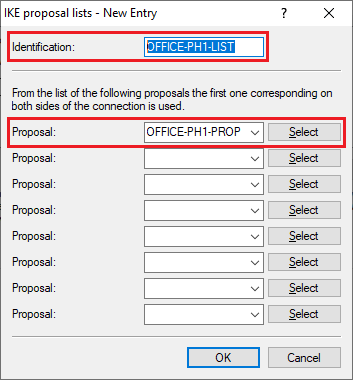
1.6) Enter the following parameters:
- Identification: Enter a descriptive name (in this example OFFICE-PH1-LIST). The key length is limited to 17 characters.
- Proposal: From the drop-down menu, select the IKE proposal created in step 1.3.
2) Adjust the IPsec lifetimes (phase 2):
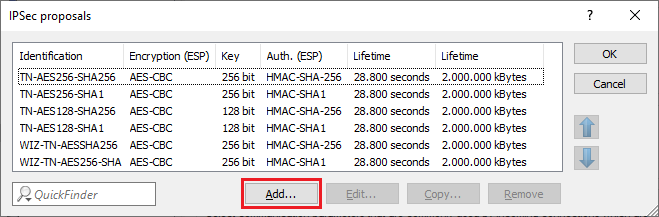
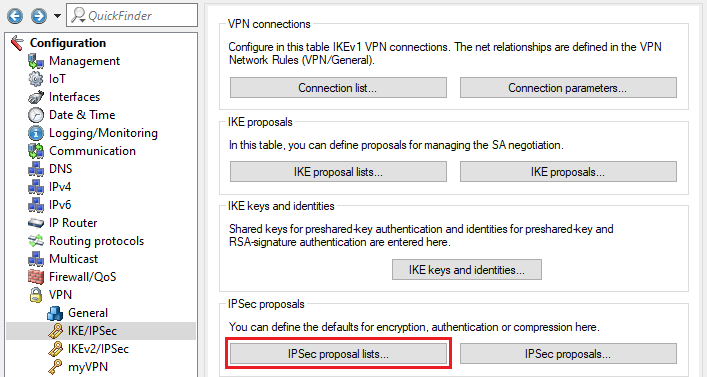
2.1) Switch to the IPsec proposals menu.
2.2) Click on Add to create a new IPsec proposal.
Under no circumstances should you edit or adapt the existing default proposals, otherwise other VPN connections that use the adapted proposal may no longer function correctly.
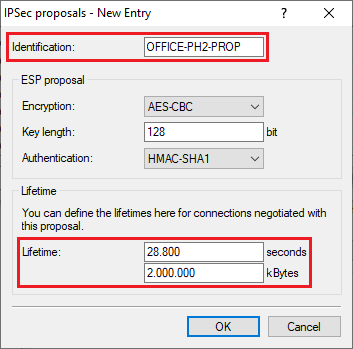
2.3) Enter the encryption settings as for the previous VPN connection and adjust the following parameters:
- Identification: Enter a descriptive name (in this example OFFICE-PH2-PROP). The key length is limited to 17 characters.
- Lifetime: Enter the required lifetime in seconds. Leave the lifetime in kBytes at the default setting 2,000,000 kBytes.
LANCOM Systems recommends a maximum lifetime of 28,800 seconds (8 hours) in combination with a data volume of 2,000,000 kBytes (corresponds to the default setting). As of November 2021, the BSI (German Federal Office for Information Security) recommends a maximum lifetime of 14,400 seconds (4 hours) for IKEv2.
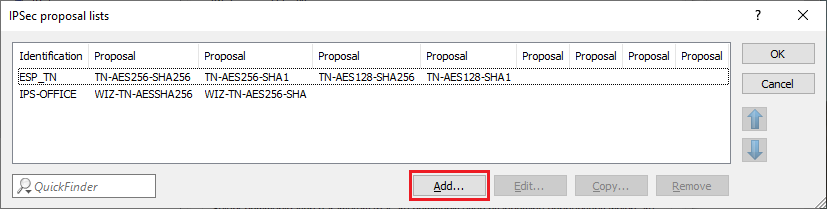
2.4) Switch to the IPsec proposal lists menu.
2.5) Click on Add to create a new IPsec proposal list.
Instead of creating a new IPsec proposal list, you can also directly edit the proposal list for the VPN connection itself (in this example IPS-VPN-OFFICE). However, make absolutely sure that it is not being used by any other VPN connections, otherwise they may no longer function properly.
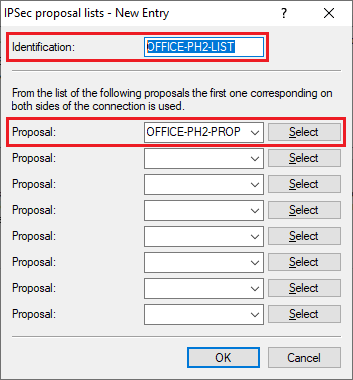
2.6) Enter the following parameters:
- Identification: Enter a descriptive name (in this example OFFICE-PH2-LIST). The key length is limited to 17 characters.
- Proposal: From the drop-down menu, select the IPsec proposal created in step 2.3.
3. Zuweisen der angepassten Proposals zu der VPN-Verbindung:
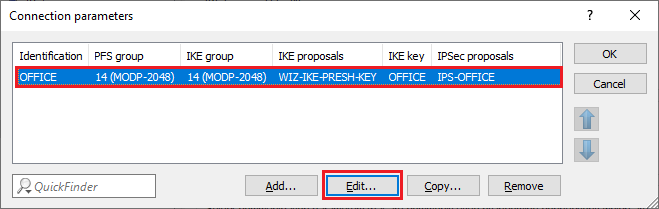
3.1 Wechseln Sie in das Menü Connection parameters.
3.2 Markieren Sie die Verbindungs-Parameter der verwendeten VPN-Verbindung und klicken auf Edit.
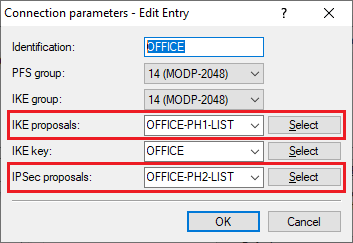
3.3 Wählen Sie im Dropdown-Menü bei IKE proposals die in Schritt 1.6 erstellte IKE proposal list und bei IPSec proposals die in Schritt 2.6 erstellte IPSec proposal list aus.
3.4 Die Anpassung der IKE- und IPSec-Lifetimes ist damit abgeschlossen. Schreiben Sie die Konfiguration in den Router zurück.
4. Neustart der VPN-Verbindung:
Damit die vorgenommenen Änderungen umgesetzt werden, muss die VPN-Verbindung neugestartet werden.
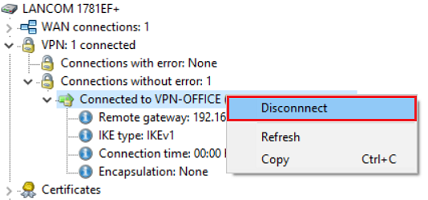
4.1 Neustart der VPN-Verbindung per LANmonitor:
Markieren Sie die VPN-Verbindung, führen einen Rechtsklick aus und wählen im Kontextmenü die Option Disconnect aus.
4.2 Neustart der VPN-Verbindung per Konsole:
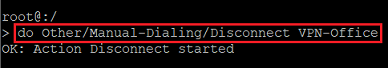
Geben Sie den Befehl zum Trennen der VPN-Verbindung im folgenden Format ein:
do Other/Manual-Dialing/Disconnect <Name of the VPN connection>
In diesem Beispiel muss der Befehl also wie folgt lauten:
do Other/Manual-Dialing/Disconnect VPN-OFFICE